CVSS Scoring & FedRAMP – What You Need to Know?
Commercial cloud service providers (CSPs) are responsible for maintaining a similar risk profile to the risks identified within their most recent Security Assessment Report (SAR). CSPs submit continuous monitoring deliverables each month for review by the FedRAMP PMO and their sponsoring agency or the Joint Authorization Board (JAB). These deliverables include a Plan of Action & Milestones (POA&M) and a Deviation Request (DR) list. FedRAMP Vulnerability Scanning Guidance from March 2018 requires that the vulnerabilities listed on these documents use the CVSSv3 calculation, when available, to determine a risk rating.
Why Does It Matter?
Often, CSPs will track risk based on their implemented vulnerability scanner’s default outputs. This can cause a mismatch between the CSP’s risk scores, and therefore remediation due dates, and the risk scores assigned within a 3PAO’s SAR.
“For any vulnerability with a CVSSv3 base score assigned in the latest version of the NVD, the CVSSv3 base score must be used as the original risk rating. If no CVSSv3 score is available, a CVSSv2 base score is acceptable where available. If no CVSS score is available, the native scanner base risk score can be used.”
Risk scores calculated via CVSSv3 are more often higher than the tool-assigned score as opposed to lower. Further, CVSSv3 scores present many vulnerabilities as High or Critical severity based on default parameters which are typically inaccurate for a FedRAMP environment.
This means that an organization that understands CVSS scoring will be able to present a lower, and more accurate risk profile to authorizing officials than an organization who does not understand CVSS scoring. Furthermore, organizations that prepare this quantitative evidence before FedRAMP assessment are able to minimize the likelihood of High-severity issues from vulnerability scan results holding up the overall FedRAMP package.
How is CVSS Score Calculated?
First.org provides an excellent detailed view of CVSS scoring specifications within their documentation resources. At a higher-level view, CVSS scoring is based on a number of metrics to evaluate the ease for an attacker to exploit a vulnerability and the potential impact of that vulnerability if it is exploited. For example, a 10 out of 10 (aka Critical) vulnerability would have high impact to confidentiality, integrity, and availability of the system and could be exploited with relative ease, across an open network, without privileged access. The ease of exploit does not consider environmental factors and is the best way for CSPs to provide both qualitative and quantitative justification for a Risk Adjustment (RA) DR.
Qualitative versus Quantitative
A strong qualitative justification, used as the content within the ‘DR Rationale’ column of the Deviation Request Form, should tie directly to the concepts within the CVSS score mentioned above. This ties the risk adjustment justification to the same metrics that originally defined it’s risk. It also tees up the re-calculation with 1:1 matches of narrative to the altered parameters in the CVSSv3 calculator. For example, “[CSP NAME] has identified this vulnerability for risk adjustment due to it being an internally-facing asset within our FedRAMP environment. In order for this vulnerability to be exploited, an attacker would require VPN access to the back-end, privileged credentials on a bastion host, and MFA for authentication into the environment.”
This narrative aligns to metrics within the calculator which are very impactful to justifying a risk adjustment.
Attack Vector (AV) – “internally-facing asset within our FedRAMP environment. In order for this vulnerability to be exploited, an attacker would require VPN access to the back-end”
Privileges Required (PR) – “privileged credentials on a bastion host”
Attack Complexity (AC) – “MFA for authentication into the environment”
Overall, a High severity vulnerability could be brought to a Medium/Moderate severity level by adjusting those three parameters:
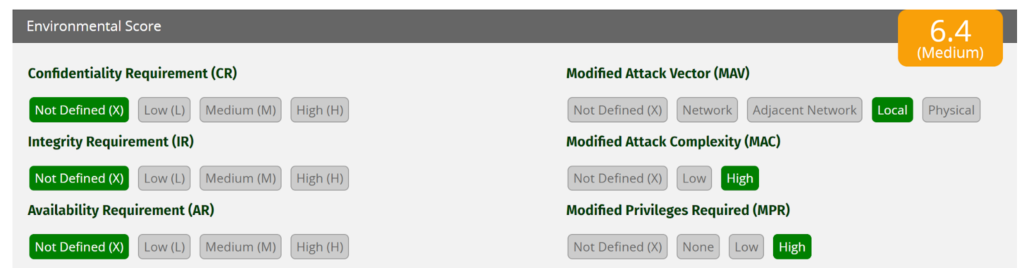
Summary
While the topic of CVSS scoring may seem in-the-weeds, it has an important role to play in an organization’s overall success within the FedRAMP program. At the end of the day, FedRAMP is a risk-based framework that relies heavily on accurate reporting of risk to a system and therefore the data processed or stored by that system. Authorizing Officials will be far less likely to issue an authorization to operate (ATO) to a CSP that has open & unmitigated High severity flaws which increases the importance of providing clear justification, both qualitative and quantitative, of the true risk.











