Overview
This summer, the Federal Risk and Management Program (FedRAMP) released Request for Comment (RFC) 0012, Continuous Vulnerability Management Standard. This proposed update introduces significant changes to how Cloud Service Providers (CSPs) assess and manage vulnerabilities within their cloud systems. Key updates include:
- Emphasis and prioritization on internet-reachable resources
- Stricter remediation timelines
- A shift in vulnerability severity calculation

Key Focus on Internet-Reachable Resources
A major shift in RFC-0012 is its focus on internet-reachable resources. These are components accessible via the public internet without requiring a VPN or other restricted access controls. Examples include public-facing web applications, load balancers, DNS servers, external APIs, and email gateways.
Under the proposed standard, CSPs are required to monitor and track the status of vulnerabilities affecting Internet-reachable affected. The proposed remedial schedule for these resources is three (3) calendar days, which is substantial reduction from the previous standards requiring thirty (30), ninety (90), and 180-day remediation timelines, for low, moderate, and high severity findings, respectively.
To support this accelerated timeline, RFC-0012 mandates continuous or near continuous scanning using both authenticated and unauthenticated methods. Although the 3-day turnaround is aggressive, if properly implemented and followed, it greatly reduces the possibility exploitation, which is crucial given that Internet-reachable resources are the first line of exposure to external threats. CSPs can enhance their response capabilities by developing or enhancing automated systems which incorporate scanning and ticketing procedures for all Internet-reachable devices. For example, a CSP can employ automated workflows to generate issue tickets using vulnerability data on assets tagged as Internet-facing.
Grouping Vulnerabilities: A New Approach
RFC-0012 also introduces an approach to vulnerability grouping, which allows CSPs to consolidate similar vulnerabilities detected across different resources into one. The grouping must be based on shared characteristics such as common root causes, affected components (package/image/version), or remediation strategies. This grouping approach could streamline remediation efforts and help address vulnerabilities in batches, potentially reducing the overall vulnerability count.
However, this approach introduces challenges with maintaining reporting consistency across CSPs and cloud authorizations. The grouping could vary depending on how the provider defines the “sensible” characteristics, which may lead to inconsistencies amongst CSPs. This, in turn, may require Third Party Assessment Organizations (3PAOs) to verify the accuracy of these groupings, complicating the tracking and monitoring of identical vulnerabilities across several systems.
Since individual open vulnerabilities won’t be tracked for each scan, the integrity of the metrics can become compromised. As a result, 3PAOs may become more reliant on the logic and procedures established by CSPs. To ensure that all impacted resources are monitored, tracked, and remediated within the necessary timeframe, 3PAOs may need to conduct more detailed audits. To support transparency, CSPs should maintain a clear mapping of grouped vulnerabilities to affected assets and be prepared to present their grouping logic during assessments.
Additionally, the US government’s ability to make public policy or national security decisions using ConMon datasets will be hindered by reduced objectivity and comparability.

A Shift from CVSS: Contextual Risk Prioritization
The Common Vulnerability Scoring System (CVSS) has consistently served as the go-to method of computing vulnerability severity in FedRAMP. CVSS versioning is used in a prioritization method, meaning CVSSv3 should be used, if CVSSv3 is unavailable, CVSSv2 may be used as the fall back; if neither is available, the scanner is permitted to employ its native score. This new version signifies a transition away from this method by emphasizing contextual risk prioritization.
Rather than solely relying on CVSS scoring, CSPs must now assess vulnerabilities based on multiple factors, including:
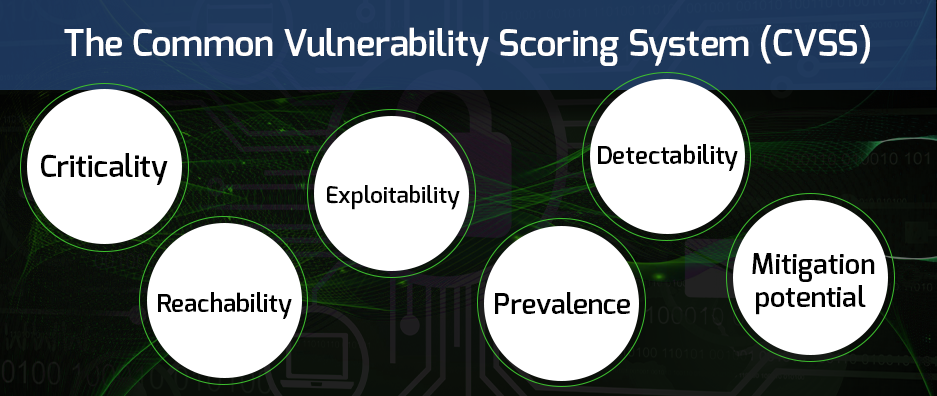
It’s important to note that some aspects of this new methodology for prioritizing findings may be redundant with CVSSv3 scoring metrics, which currently allows for modification of environmental and temporal factors such as:
- Attack Vector
- Attack Complexity
- Privileges Required
- User Interaction
- Scope
- Confidentiality
- Integrity
- Availability
- Exploit Code Maturity
- Remediation Levels
- Report Confidence
Adhering to the revised process may increase the workload for CSP teams conducting vulnerability investigations and analysis. This may require dedicated teams for in–depth vulnerability analysis, particularly given that some large-scale systems report thousands of vulnerabilities in a single scan. However, this approach enables more precise remediation timelines which align with actual risk. This will allow CSPs to focus on a select few high-priority vulnerabilities that pose the greatest threat to their environment rather than addressing all vulnerabilities categorized as “High” based on the CVSS score system. Additionally, the enrichment process for Common Vulnerabilities and Exposures (CVEs) is often delayed which further reduces the usability of CVSS scores.
Encouraging Urgent Mitigation of Vulnerabilities
RFC-0012 mandates rapid mitigation when full remediation is not immediately feasible. For Internet-reachable systems, mitigation must occur within three (3) calendar days; for other systems, within twenty-one (21) days. An exception is made if the potential adverse impact is assessed to be “very low.”
This emphasis on urgent mitigation is consistent with the real-world threat dynamics, since adversaries frequently exploit unpatched but publicly known vulnerabilities within days of their disclosure. Although this could lead to the need for CSPs to invest additional effort in developing automated tools to manage the sheer volume of new mitigations, it ultimately will enable CSPs to adopt a proactive position on vulnerability management.

Conclusion
The proposed Vulnerability Management Standard 0012 signifies a substantial change in the approach that CSPs must adopt for their Vulnerability Management Program. It emphasizes urgent mitigations, prioritization of Internet-accessible resources, enforcement of stricter remediation timelines, and assessment of risk that extends beyond CVSS scoring. While these changes offer CSPs the chance to enhance their security posture and their vulnerability management processes, they may also introduce a set of operational and compliance challenges.
As CSPs prepare for these changes in FedRAMP, it’s important to stay informed of some key timelines. During the “FedRAMP Vulnerability Management Special Event” that took place on July 30th, 2025, it was announced that a closed beta for RFC-0012 would be released following the public comment period, which concludes on August 21st. A public beta will follow, with a full release anticipated within the next 6-9 months. During which time, specific timelines will be established for when CSPs must transition to the revised standards. To ensure a smooth transition, CSPs should stay proactive in monitoring these timelines and aligning internal processes and procedures with the forthcoming revisions.
Fortreum is an independent firm specializing in audit, advisory, and technical testing services, delivering cybersecurity expertise in highly regulated industries. Our mission is to simplify cloud and cybersecurity challenges for our clients. With nearly 25 years of combined experience in both the public and private sectors, Fortreum is dedicated to addressing our customers’ complex cloud and cybersecurity needs.
For more information, visit the Fortreum website or follow the company on LinkedIn at LinkedIn.com/company/fortreum.
Should you have questions about your PCI, FedRAMP, XRAMP, cloud and cybersecurity readiness, please reach out to us at Info@fortreum.com or Contact Us at https://fortreum.com/contact/