FedRAMP - Major Regulatory Release
(NIST SP 800-53 Rev. 4 to Rev. 5)
Abstract
In 2020, the National Institute for Standards and Technology (NIST) published the final version of SP 800-53 Revision 5 and SP 800-53B, Control Baselines for Information Systems and Organizations. This represents a multi-year effort to develop a more reflective security and privacy controls integration. While the framework natively still applies only to federal agencies and their information systems, NIST is encouraging the document to be more applicable to both non-federal and private organizations
The FedRAMP PMO has since worked with the Joint Authorization Board (JAB) over that time to further develop the FedRAMP baselines in alignment with NIST’s Rev. 5 update (draft most recently published December 21, 2021). As noted in NIST and FedRAMP PMO notices, key changes to the security requirements are more on threat-based methodologies (outcome based), empirical attack data, systems engineering, and supply chain best practices.
This post is intended to provide FedRAMP stakeholders (CSP’s, 3PAO’s, Federal Agencies, Research Institutions) better visibility into the FedRAMP draft release of NIST SP 800-53 Rev. 5 to assist in your data analysis for the upcoming comment period, technical, and business impacts.
Aggregate FedRAMP View (NIST SP 800-53 Rev. 4 to Rev. 5 Comparison)
- Low Baseline – FedRAMP added 1 additional control (above the NIST baseline)
- Moderate Baseline – FedRAMP added 17 additional controls (above the NIST baseline)
- High Baseline – FedRAMP added 22 additional controls (above the NIST baseline)
|
|
High Baseline |
Moderate Baseline |
Low Baseline |
|
FedRAMP (Rev 4) Baseline |
421 |
325 |
125 |
|
Controls & Enhancements withdrawn (FedRAMP PMO and NIST) |
-74 |
-62 |
-3 |
|
Subtotal |
347 |
263 |
122 |
|
FedRAMP & NIST (Rev 5) Controls Added* |
+45 |
+41 |
+28 |
|
Subtotal |
392 |
304 |
150 |
|
Controls withdrawn, but consolidated/ merged* |
+21 |
+16 |
+2 |
|
Total |
413 |
320 |
152 |
|
*Withdrawn controls consolidated to a new control were not counted twice |
|||
FedRAMP Control Parameter Changes
Security control parameter changes should also be taken into consideration when looking to evaluate the security control deltas. Due to the timing of the release and our feedback, we wanted to get out some initial thoughts out. We will have a follow-up to this blog with the parameter changes once the PMO baseline is considered final.
Let Your Voice Be Heard
Published in earlier guidance – the FedRAMP PMO has established a general timeline on how the review process will proceed. This is very similar to the standard NIST publications/releases.
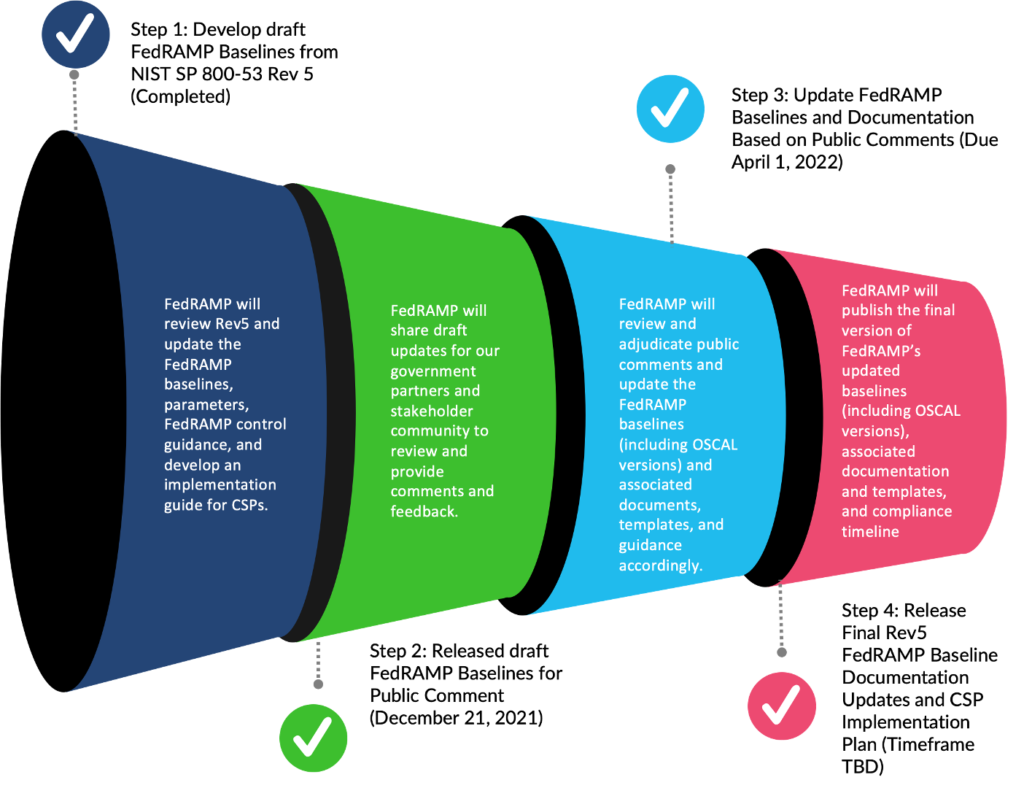
It’s important that the FedRAMP business community get involved to ensure a more refined work product in the end.
- Cloud Service Providers (CSP) – look to understand what’s being asked of you. What material differences can you identify? What feedback can you give the FedRAMP PMO to promote a reasonable interpretation of the requirements and security risk?
- Third Party Assessment Organizations (3PAO) – understand the requirements (withdrawn, consolidated, and net-new). Do your own analysis and determine any material changes within the new proposed baseline. What’s missing? How do you advise or test the CSP’s against these requirements?
- Government direct and research community stakeholders – it’s really important that your feedback is part of the baseline. The more integrated the FedRAMP baseline is from the viewpoint of an agency, the more reciprocity is achieved across government.
- Industry Best Practice stakeholders – promoting industry best practices amongst our government should be a civic duty. Share your thoughts and insights to ensure this truly is the greatest good security requirements and practices for government.
The FedRAMP PMO has released an initial draft of the FedRAMP Rev. 5 for your review and comment. As noted in the release, industry feedback will be accepted through info@fedramp.gov via this format by Friday, April 1, 2022.
Historically speaking, a similar approach was taken when FedRAMP released the initial baseline associated with NIST SP 800-53 Rev. 4. CSPs were provided a period of time to review the new controls, provide feedback on if the parameter was accurate or if the control should even be included in the baseline. After that time period came and went, FedRAMP finalized their baseline for all to use. At that time, it was not an instantaneous adoption. FedRAMP worked with each CSP to determine at what point in the process would they look to uplift to the new baseline. This is primarily because new security controls must first be implemented and that just doesn’t happen overnight. FedRAMP knows this. You will have time to implement the controls and then have it properly tested by your 3PAO.
FedRAMP has not officially said what that the time period will look like, but if history repeats itself, it may look similar to something like this:
- CSPs with an existing ATO will uplift to the new baseline at their next annual, or the one after, depending on the ATO date
- If a CSP is in the middle of their initial assessment, they will be allowed to continue under NIST SP 800-53 Rev. 4, but will be expected to uplift to Rev. 5 during their first annual
- If a CSP is in the early stages of FedRAMP preparation and has not started an assessment, it will truly depend how early it is in the process. However most likely, these CSPs will need to look at the new baseline and have a strategy around how those new controls will be implemented. This will probably be handled on a case-by-case basis with the CSP and the FedRAMP PMO.
Summary
Major releases of the NIST SP 800-53 security guidance does not come along often and takes several years to be fully evaluated, revised, impacted, and implemented.
The number of security controls (plus or minus) does not necessarily equate level of effort or material impacts from a regulation perspective. Complexity of the control, parameter changes (frequency/how restrictive) and technical feasibility for the cloud service provider to implement is what will drive impacts on what these regulations mean to the FedRAMP community. Another key aspect to consider is the shared responsibility model with underlying infrastructure as a service or platform as a service provider. This new baseline will impact the number of controls or portions of controls are fully inherited or partially inherited by these providers.
As noted above, take the time to review and provide feedback. You can’t complain about the process if you haven’t taken the time to response and be heard.
Our initial review and research are providing a more detailed view into potential impacts (Draft release from the FedRAMP PMO – subject to change based on feedback), but further research and discussions will be needed to better understand material impacts. Fortreum will look to release more content in the future (especially once this publication is final) to assist the FedRAMP community in understanding the full impacts of these changes.
Appendix A: Key Control Considerations
Control Family | Controls | Control Name |
Identification and Authentication | IA-05 (11)* | Authenticator Management | Hardware Token-based Authentication |
Identification and Authentication | IA-08 (03)* | Identification and Authentication | Use of FICAM-Approved Products |
System and Information Integrity | SI-16 | Memory Protection |
*Indicates controls removed from NIST 800-53 Rev. 5 but consolidated into another control in the baseline.
Controls Removed from the FedRAMP Moderate Baseline (62)
Control Family | Controls | Control Name |
Access Control | AC-02 (10)* | Account Management | Shared / Group Account Credential Termination |
Access Control | AC-04 (21) | Information Flow Enforcement | Physical / Logical Separation of Information Flows |
Access Control | AC-10 | Concurrent Session Control |
Access Control | AC-17 (09) | Remote Access | Disconnect / Disable Access |
Audit and Accountability | AU-02 (03)* | Audit Events | Reviews and Updates |
Audit and Accountability | AU-08 (01) | Time Stamps | Synchronization with Authoritative Time Source |
Audit and Accountability | AU-09 (02) | Protection Of Audit Information | Store on Separate Physical Systems Or Components |
Security Assessment and Authorization | CA-02 (02) | Control Assessments | Specialized Assessments |
Security Assessment and Authorization | CA-02 (03) | Security Assessments | External Organizations |
Security Assessment and Authorization | CA-03 (03) | System Interconnections | Unclassified Non-National Security System Connections |
Security Assessment and Authorization | CA-03 (05) | System Interconnections | Restrictions on External System Connections |
Security Assessment and Authorization | CA-08 | Penetration Testing |
Security Assessment and Authorization | CA-08 (01) | Penetration Testing | Independent Penetration Testing Agent or Team |
Configuration Management | CM-02 (01)* | Baseline Configuration | Reviews and Updates |
Configuration Management | CM-05 (03) | Access Restrictions for Change | Signed Components |
Configuration Management | CM-08 (05)* | Information System Component Inventory | No Duplicate Accounting of Components |
Configuration Management | CM-10 (01) | Software Usage Restrictions | Open-Source Software |
Contingency Planning | CP-02 (02) | Contingency Plan | Capacity Planning |
Contingency Planning | CP-09 (03) | System Backup | Separate Storage for Critical Information |
Identification and Authentication | IA-02 (03)* | Identification And Authentication | Local Access to Privileged Accounts |
Identification and Authentication | IA-02 (11)* | Identification And Authentication | Remote Access – Separate Device |
Identification and Authentication | IA-05 (03)* | Authenticator Management | In-Person or Trusted Third-Party Registration |
Identification and Authentication | IA-05 (04)* | Authenticator Management | Automated Support for Password Strength Determination |
Identification and Authentication | IA-05 (11)* | Authenticator Management | Hardware Token-Based Authentication |
Identification and Authentication | IA-08 (03)* | Identification And Authentication | Use of FICAM-Approved Products |
Incident Response | IR-07 (02) | Incident Response Assistance | Coordination with External Providers |
Incident Response | IR-09 | Information Spillage Response |
Incident Response | IR-09 (01) | Information Spillage Response | Responsible Personnel |
Incident Response | IR-09 (02) | Information Spillage Response | Training |
Incident Response | IR-09 (03) | Information Spillage Response | Post-Spill Operations |
Incident Response | IR-09 (04) | Information Spillage Response | Exposure to Unauthorized Personnel |
Maintenance | MA-04 (02)* | Nonlocal Maintenance | Document Nonlocal Maintenance |
Maintenance | MA-05 (01) | Maintenance Personnel | Individuals Without Appropriate Access |
Media Protection | MP-05 (04)* | Media Transport | Cryptographic Protection |
Media Protection | MP-06 (02) | Media Sanitization | Equipment Testing |
Media Protection | MP-07 (01)* | Media Use | Prohibit Use Without Owner |
Physical and Environmental Protection | PE-13 (02) | Fire Protection | Suppression Systems — Automatic Activation and Notification |
Physical and Environmental Protection | PE-13 (03)* | Fire Protection | Automatic Fire Suppression |
Physical and Environmental Protection | PE-14 (02) | Temperature And Humidity Controls | Monitoring with Alarms / Notifications |
Planning | PL-02 (03)* | System Security Plan | Plan / Coordinate with Other Organizational Entities |
Personnel Security | PS-03 (03) | Personnel Screening | Information with Special Protection Measures |
Risk Assessment | RA-05 (01)* | Vulnerability Scanning | Update Tool Capability |
Risk Assessment | RA-05 (06) | Vulnerability Scanning | Automated Trend Analyses |
Risk Assessment | RA-05 (08) | Vulnerability Scanning | Review Historic Audit Logs |
System and Services Acquisition | SA-04 (08) | Acquisition Process | Continuous Monitoring Plan |
System and Services Acquisition | SA-09 (01) | External Information Systems | Risk Assessments / Organizational Approvals |
System and Services Acquisition | SA-09 (04) | External Information Systems | Consistent Interests of Consumers and Providers |
System and Services Acquisition | SA-09 (05) | External System Services | Processing, Storage, And Service Location |
System and Services Acquisition | SA-10 (01) | Developer Configuration Management | Software / |
System and Services Acquisition | SA-11 (01) | Developer Security Testing and Evaluation | Static Code Analysis |
System and Services Acquisition | SA-11 (02) | Developer Security Testing and Evaluation | Threat and Vulnerability Analyses |
System and Services Acquisition | SA-11 (08) | Developer Security Testing and Evaluation | Dynamic Code Analysis |
System and Communications Protection | SC-06 | Resource Availability |
System and Communications Protection | SC-07 (13) | Boundary Protection | Isolation of Security Tools / |
System and Communications Protection | SC-12 (02) | Cryptographic Key Establishment and Management | |
System and Communications Protection | SC-12 (03) | Cryptographic Key Establishment and Management | |
System and Communications Protection | SC-19 | Voice Over Internet Protocol |
System and Information Integrity | SI-03 (01) | Malicious Code Protection | Central Management |
System and Information Integrity | SI-03 (02)* | Malicious Code Protection | Automatic Updates |
System and Information Integrity | SI-03 (07)* | Malicious Code Protection | Nonsignature-Based Detection |
System and Information Integrity | SI-04 (14) | System Monitoring | Wireless Intrusion Detection |
System and Information Integrity | SI-08 (01) | Spam Protection | Central Management |
*Indicates controls removed from NIST 800-53 Rev. 5 but consolidated into another control in the baseline.
Controls Removed from the FedRAMP High Baseline (74)
Control Family | Controls | Control Name |
Access Control | AC-02 (10)* | Account Management | Shared / Group Account Credential Termination |
Access Control | AC-04 (08) | Information Flow Enforcement | Security Policy Filters |
Access Control | AC-04 (21) | Information Flow Enforcement | Physical / Logical Separation of Information Flows |
Access Control | AC-07 (02) | Unsuccessful Logon Attempts | Purge / Wipe Mobile Device |
Access Control | AC-12 (01) | Session Termination | User-Initiated Logouts / Message Displays |
Access Control | AC-17 (09) | Remote Access | Disconnect / Disable Access |
Awareness and Training | AT-03 (03) | Security Training | Practical Exercises |
Awareness and Training | AT-03 (04) | Security Training | Suspicious Communications and Anomalous System Behavior |
Audit and Accountability | AU-02 (03)* | Audit Events | Reviews and Updates |
Audit and Accountability | AU-03 (02) | Content Of Audit Records | Centralized Management Of Planned Audit Record Content |
Audit and Accountability | AU-06 (10)* | Audit Review, Analysis, And Reporting | Audit Level Adjustment |
Audit and Accountability | AU-08 (01) | Time Stamps | Synchronization with Authoritative Time Source |
Security Assessment and Authorization | CA-02 (03) | Security Assessments | External Organizations |
Security Assessment and Authorization | CA-03 (03) | System Interconnections | Unclassified Non-National Security System Connections |
Security Assessment and Authorization | CA-03 (05) | System Interconnections | Restrictions on External System Connections |
Security Assessment and Authorization | CA-07 (03) | Continuous Monitoring | Trend Analyses |
Configuration Management | CM-02 (01)* | Baseline Configuration | Reviews and Updates |
Configuration Management | CM-05 (02) | Access Restrictions for Change | Review System Changes |
Configuration Management | CM-05 (03) | Access Restrictions for Change | Signed Components |
Configuration Management | CM-08 (05)* | Information System Component Inventory | No Duplicate Accounting of Components |
Configuration Management | CM-10 (01) | Software Usage Restrictions | Open-Source Software |
Configuration Management | CM-11 (01)* | User-Installed Software | Alerts for Unauthorized Installations |
Contingency Planning | CP-02 (04)* | Contingency Plan | Resume All Missions / Business Functions |
Identification and Authentication | IA-02 (03)* | Identification And Authentication | Local Access to Privileged Accounts |
Identification and Authentication | IA-02 (04)* | Identification And Authentication | Local Access to Non-Privileged Accounts |
Identification and Authentication | IA-02 (09)* | Identification And Authentication | Network Access to Non-Privileged Accounts – Replay Resistant |
Identification and Authentication | IA-02 (11)* | Identification And Authentication | Remote Access – Separate Device |
Identification and Authentication | IA-05 (03)* | Authenticator Management | In-Person or Trusted Third-Party Registration |
Identification and Authentication | IA-05 (04)* | Authenticator Management | Automated Support for Password Strength Determination |
Identification and Authentication | IA-05 (11)* | Authenticator Management | Hardware Token-Based Authentication |
Identification and Authentication | IA-08 (03)* | Identification And Authentication | Use of FICAM-Approved Products |
Incident Response | IR-04 (03) | Incident Handling | Continuity of Operations |
Incident Response | IR-04 (08) | Incident Handling | Correlation with External Organizations |
Incident Response | IR-07 (02) | Incident Response Assistance | Coordination with External Providers |
Incident Response | IR-09 | Information Spillage Response |
Incident Response | IR-09 (01) | Information Spillage Response | Responsible Personnel |
Incident Response | IR-09 (02) | Information Spillage Response | Training |
Incident Response | IR-09 (03) | Information Spillage Response | Post-Spill Operations |
Incident Response | IR-09 (04) | Information Spillage Response | Exposure to Unauthorized Personnel |
Maintenance | MA-04 (02)* | Nonlocal Maintenance | Document Nonlocal Maintenance |
Maintenance | MA-04 (06) | Nonlocal Maintenance | Cryptographic Protection |
Media Protection | MP-05 (04)* | Media Transport | Cryptographic Protection |
Media Protection | MP-07 (01)* | Media Use | Prohibit Use Without Owner |
Physical and Environmental Protection | PE-13 (03)* | Fire Protection | Automatic Fire Suppression |
Physical and Environmental Protection | PE-14 (02) | Temperature And Humidity Controls | Monitoring with Alarms / Notifications |
Planning | PL-02 (03)* | System Security Plan | Plan / Coordinate with Other Organizational Entities |
Personnel Security | PS-03 (03) | Personnel Screening | Information with Special Protection Measures |
Risk Assessment | RA-05 (01)* | Vulnerability Scanning | Update Tool Capability |
Risk Assessment | RA-05 (06) | Vulnerability Scanning | Automated Trend Analyses |
Risk Assessment | RA-05 (08) | Vulnerability Scanning | Review Historic Audit Logs |
Risk Assessment | RA-05 (10) | Vulnerability Scanning | Correlate Scanning Information |
System and Services Acquisition | SA-04 (08) | Acquisition Process | Continuous Monitoring Plan |
System and Services Acquisition | SA-09 (01) | External Information Systems | Risk Assessments / |
System and Services Acquisition | SA-09 (04) | External Information Systems | Consistent Interests of Consumers and Providers |
System and Services Acquisition | SA-10 (01) | Developer Configuration Management | Software / |
System and Services Acquisition | SA-11 (01) | Developer Security Testing and Evaluation | Static Code Analysis |
System and Services Acquisition | SA-11 (02) | Developer Security Testing and Evaluation | Threat and Vulnerability Analyses |
System and Services Acquisition | SA-11 (08) | Developer Security Testing and Evaluation | Dynamic Code Analysis |
System and Services Acquisition | SA-12* | Supply Chain Protection |
System and Communications Protection | SC-06 | Resource Availability |
System and Communications Protection | SC-07 (10) | Boundary Protection | Prevent Unauthorized Exfiltration |
System and Communications Protection | SC-07 (13) | Boundary Protection | Isolation of Security Tools / |
System and Communications Protection | SC-12 (02) | Cryptographic Key Establishment and Management | |
System and Communications Protection | SC-12 (03) | Cryptographic Key Establishment and Management | |
System and Communications Protection | SC-19 | Voice Over Internet Protocol |
System and Communications Protection | SC-23 (01) | Session Authenticity | Invalidate Session Identifiers at Logout |
System and Information Integrity | SI-02 (01) | Flaw Remediation | Central Management |
System and Information Integrity | SI-03 (01) | Malicious Code Protection | Central Management |
System and Information Integrity | SI-03 (02)* | Malicious Code Protection | Automatic Updates |
System and Information Integrity | SI-03 (07)* | Malicious Code Protection | Non signature-Based Detection |
System and Information Integrity | SI-04 (18) | Information System Monitoring | Analyze Traffic / Covert Exfiltration |
System and Information Integrity | SI-04 (24) | Information System Monitoring | Indicators of Compromise |
System and Information Integrity | SI-07 (14) | Software, Firmware, And Information Integrity | Binary or Machine Executable Code |
System and Information Integrity | SI-08 (01) | Spam Protection | Central Management |
*Indicates controls removed from NIST 800-53 Rev. 5 but consolidated into another control in the baseline.
Controls Added to the FedRAMP Low Baseline (28)
Control Family | Controls | Control Name |
Awareness and Training | AT-02 (02) | Literacy Training and Awareness | Insider Threat |
Security Assessment and Authorization | CA-07 (04) | Continuous Monitoring | Risk Monitoring |
Configuration Management | CM-05 | Access Restrictions for Change |
Identification and Authentication | IA-02 (02) | Identification And Authentication (Organizational Users) | Multi-Factor Authentication to Non-Privileged Accounts |
Identification and Authentication | IA-02 (08) | Identification And Authentication (Organizational Users) | Access to Accounts — Replay Resistant |
Identification and Authentication | IA-11 | Re-Authentication |
Planning | PL-04 (01) | Rules Of Behavior | social media And External Site/Application Usage Restrictions |
Planning | PL-10 | Baseline Selection |
Planning | PL-11 | Baseline Tailoring |
Personnel Security | PS-09 | Position Descriptions |
Risk Assessment | RA-03 (01) | Risk Assessment | Supply Chain Risk Assessment |
Risk Assessment | RA-05 (02) | Vulnerability Monitoring and Scanning | Update Vulnerabilities to be Scanned |
Risk Assessment | RA-05 (11) | Vulnerability Monitoring and Scanning | Public Disclosure Program |
Risk Assessment | RA-07 | Risk Response |
System and Services Acquisition | SA-04 (10) | Acquisition Process | Use of Approved PIV Products |
System and Services Acquisition | SA-08 | Security And Privacy Engineering Principles |
System and Services Acquisition | SA-22 | Unsupported System Components |
Supply Chain Risk Management Family | SR-01 | Policy And Procedures |
Supply Chain Risk Management Family | SR-02 | Supply Chain Risk Management Plan |
Supply Chain Risk Management Family | SR-02 (01) | Supply Chain Risk Management Plan | Establish SCRM Team |
Supply Chain Risk Management Family | SR-03 | Supply Chain Controls and Processes |
Supply Chain Risk Management Family | SR-05 | Acquisition Strategies, Tools, and Methods |
Supply Chain Risk Management Family | SR-08 | Notification Agreements |
Supply Chain Risk Management Family | SR-10 | Inspection Of Systems or Components |
Supply Chain Risk Management Family | SR-11 | Component Authenticity |
Supply Chain Risk Management Family | SR-11 (01) | Component Authenticity | Anti-Counterfeit Training |
Supply Chain Risk Management Family | SR-11 (02) | Component Authenticity | Configuration Control for Component Service And Repair |
Supply Chain Risk Management Family | SR-12 | Component Disposal |
Controls Added to the FedRAMP Moderate Baseline (41)
Control Family | Controls | Control Name |
Access Control | AC-02 (13) | Account Management | Disable Accounts for High-Risk Individuals |
Access Control | AC-06 (07) | Least Privilege | Review of User Privileges |
Access Control | AC-18 (03) | Wireless Access | Disable Wireless Networking |
Awareness and Training | AT-02 (03) | Literacy Training and Awareness | Social Engineering And Mining |
Security Assessment and Authorization | CA-07 (04) | Continuous Monitoring | Risk Monitoring |
Configuration Management | CM-03 (02) | Configuration Change Control | Testing, Validation, and Documentation of Changes |
Configuration Management | CM-03 (04) | Configuration Change Control | Security and Privacy Representatives |
Configuration Management | CM-04 (02) | Impact Analyses | Verification of Controls |
Configuration Management | CM-12 | Information Location |
Configuration Management | CM-12 (01) | Information Location | Automated Tools to Support Information Location |
Contingency Planning | CP-09 (08) | System Backup | Cryptographic Protection |
Identification and Authentication | IA-02 (06) | Identification and Authentication (Organizational Users) | Access to Accounts —Separate Device |
Identification and Authentication | IA-11 | Re-Authentication |
Identification and Authentication | IA-12 | Identity Proofing |
Identification and Authentication | IA-12 (02) | Identity Proofing | Identity Evidence |
Identification and Authentication | IA-12 (03) | Identity Proofing | Identity Evidence Validation and Verification |
Identification and Authentication | IA-12 (05) | Identity Proofing | Address Confirmation |
Incident Response | IR-06 (03) | Incident Reporting | Supply Chain Coordination |
Physical and Environmental Protection | PE-13 (01) | Fire Protection | Detection Systems — Automatic Activation and Notification |
Planning | PL-10 | Baseline Selection |
Planning | PL-11 | Baseline Tailoring |
Personnel Security | PS-09 | Position Descriptions |
Risk Assessment | RA-03 (01) | Risk Assessment | Supply Chain Risk Assessment |
Risk Assessment | RA-05 (11) | Vulnerability Monitoring and Scanning | Public Disclosure Program |
Risk Assessment | RA-07 | Risk Response |
Risk Assessment | RA-09 | Criticality Analysis |
System and Services Acquisition | SA-15 | Development Process, Standards, and Tools |
System and Services Acquisition | SA-15 (03) | Development Process, Standards, and Tools | Criticality Analysis |
System and Services Acquisition | SA-22 | Unsupported System Components |
Supply Chain Risk Management Family | SR-01 | Policy And Procedures |
Supply Chain Risk Management Family | SR-02 | Supply Chain Risk Management Plan |
Supply Chain Risk Management Family | SR-02 (01) | Supply Chain Risk Management Plan | Establish SCRM Team |
Supply Chain Risk Management Family | SR-03 | Supply Chain Controls and Processes |
Supply Chain Risk Management Family | SR-05 | Acquisition Strategies, Tools, and Methods |
Supply Chain Risk Management Family | SR-06 | Supplier Assessments and Reviews |
Supply Chain Risk Management Family | SR-08 | Notification Agreements |
Supply Chain Risk Management Family | SR-10 | Inspection of Systems or Components |
Supply Chain Risk Management Family | SR-11 | Component Authenticity |
Supply Chain Risk Management Family | SR-11 (01) | Component Authenticity | Anti-Counterfeit Training |
Supply Chain Risk Management Family | SR-11 (02) | Component Authenticity | Configuration Control for Component Service and Repair |
Supply Chain Risk Management Family | SR-12 | Component Disposal |
Controls Added to the FedRAMP High Baseline (45)
Control Family | Controls | Control Name |
Access Control | AC-04 (04) | Information Flow Enforcement | Flow Control of Encrypted Information |
Awareness and Training | AT-02 (03) | Literacy Training and Awareness | Social Engineering And Mining |
Security Assessment and Authorization | CA-03 (06) | Information Exchange | Transfer Authorizations |
Security Assessment and Authorization | CA-07 (04) | Continuous Monitoring | Risk Monitoring |
Configuration Management | CM-04 (02) | Impact Analyses | Verification of Controls |
Configuration Management | CM-12 | Information Location |
Configuration Management | CM-12 (01) | Information Location | Automated Tools to Support Information Location |
Contingency Planning | CP-09 (08) | System Backup | Cryptographic Protection |
Identification and Authentication | IA-02 (06) | Identification And Authentication (Organizational Users) | Access to Accounts —Separate Device |
Identification and Authentication | IA-11 | Re-Authentication |
Identification and Authentication | IA-12 | Identity Proofing |
Identification and Authentication | IA-12 (02) | Identity Proofing | Identity Evidence |
Identification and Authentication | IA-12 (03) | Identity Proofing | Identity Evidence Validation and Verification |
Identification and Authentication | IA-12 (04) | Identity Proofing | In-Person Validation and Verification |
Identification and Authentication | IA-12 (05) | Identity Proofing | Address Confirmation |
Incident Response | IR-04 (11) | Incident Handling | Integrated Incident Response Team |
Incident Response | IR-06 (03) | Incident Reporting | Supply Chain Coordination |
Planning | PL-10 | Baseline Selection |
Planning | PL-11 | Baseline Tailoring |
Personnel Security | PS-09 | Position Descriptions |
Risk Assessment | RA-03 (01) | Risk Assessment | Supply Chain Risk Assessment |
Risk Assessment | RA-05 (11) | Vulnerability Monitoring and Scanning | Public Disclosure Program |
Risk Assessment | RA-07 | Risk Response |
Risk Assessment | RA-09 | Criticality Analysis |
System and Services Acquisition | SA-04 (05) | Acquisition Process | System, Component, And Service Configurations |
System and Services Acquisition | SA-15 (03) | Development Process, Standards, and Tools | Criticality Analysis |
System and Services Acquisition | SA-21 | Developer Screening |
System and Services Acquisition | SA-22 | Unsupported System Components |
System and Information Integrity | SI-04 (10) | System Monitoring | Visibility of Encrypted Communications |
System and Information Integrity | SI-04 (12) | System Monitoring | Automated Organization-Generated Alerts |
System and Information Integrity | SI-07 (15) | Software, Firmware, and Information Integrity | Code Authentication |
Supply Chain Risk Management Family | SR-01 | Policy And Procedures |
Supply Chain Risk Management Family | SR-02 | Supply Chain Risk Management Plan |
Supply Chain Risk Management Family | SR-02 (01) | Supply Chain Risk Management Plan | Establish SCRM Team |
Supply Chain Risk Management Family | SR-03 | Supply Chain Controls and Processes |
Supply Chain Risk Management Family | SR-05 | Acquisition Strategies, Tools, And Methods |
Supply Chain Risk Management Family | SR-06 | Supplier Assessments and Reviews |
Supply Chain Risk Management Family | SR-08 | Notification Agreements |
Supply Chain Risk Management Family | SR-09 | Tamper Resistance and Detection |
Supply Chain Risk Management Family | SR-09 (01) | Tamper Resistance and Detection | Multiple Stages of System Development Life Cycle |
Supply Chain Risk Management Family | SR-10 | Inspection of Systems or Components |
Supply Chain Risk Management Family | SR-11 | Component Authenticity |
Supply Chain Risk Management Family | SR-11 (01) | Component Authenticity | Anti-Counterfeit Training |
Supply Chain Risk Management Family | SR-11 (02) | Component Authenticity | Configuration Control for Component Service and Repair |
Supply Chain Risk Management Family | SR-12 | Component Disposal |











