Table of Content
FedRAMP NIST SP 800-53 Rev 4 to Rev 5 Impacts
The long-awaited Federal Risk and Authorization Management Program (FedRAMP) release of the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53 Revision (Rev) 5 controls has been published as of May 30, 2023. These new security controls and selected subset of controls are based on the evolving need to evaluate a Cloud Service Provider’s (CSP) risk maturity and FedRAMP activity/readiness and to further mitigate risk. With the final release of the Rev 5 baselines by the FedRAMP Program Management Office (PMO), FedRAMP CSPs are asking, “What does this mean for my organization”? or “What steps can my organization take to successfully transition to Rev 5″? As a leading FedRAMP Third-Party Assessment Organization (3PAO), we are looking to impact the deltas and material impacts.
Key points covered in this content update include:
- Develop Transition Plan from Rev 4 to Rev 5 by determining technical, process, and documentation impacts to the CSP’s authorization timeline with a best path forward approach
- Determine impacts to the CSP’s FedRAMP authorization timeline – determine what phase and impact to current and/or upcoming annual assessments
- Determine technology, documentation, and boundary Impacts by conducting a Gap Assessment against Rev 5’s delta controls
- Technical Testing Impacts. Identify possible impacts to penetration testing and vulnerability management support services
Our goal is to provide CSPs with a business level summary and outline key considerations in developing a Rev 5 transition plan.
Key Point 1: Rev 4 to Rev 5 Transition
Key Point 2: Impacts to CSPs with a Current FedRAMP Authorization
The details in the following sections are only for CSPs with an active FedRAMP Joint Authorization Board (JAB) or Agency authorization. Any CSPs that would like to submit a package for their initial authorization under Rev 4 will need pre-approval from either the JAB, Agency, or the PMO.
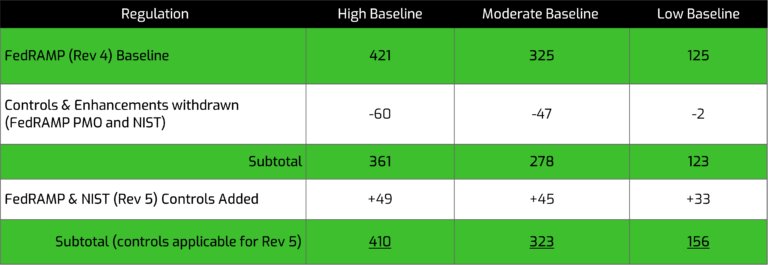
As we evaluated the FedRAMP PMO Rev 5 guidance changes, we wanted to also include impacts from the Rev 4 to Rev 5 FedRAMP security control perspective. Summarized below are some of the key counts of changes incorporated into the final Rev 5 control set.

While a lot of controls changed locations under Rev 5, there are still a decent number of new controls to consider for the next annual assessment. All net-new controls are:
- required to be assessed in the annual assessment
- included in the control-based plan of action and milestones
- included in the annually required controls[1]
- included in any remaining subset of security controls to ensure each control is still satisfied over the required 3-year cycle
Even though each CSP is unique in how their controls are split amongst the 3-year cycle, it is anticipated that the number of controls to be tested for the first Rev 5 annual assessment is going to be higher than previous annual assessments. The table below details the anticipated impact on the control selection for annual assessments. For more information about the control changes, FedRAMP PMO also provided a Rev. 4 to Rev. 5 comparison spreadsheet – can be found here.
[1] The annually required controls are still in the process of being updated to reflect Rev 5.
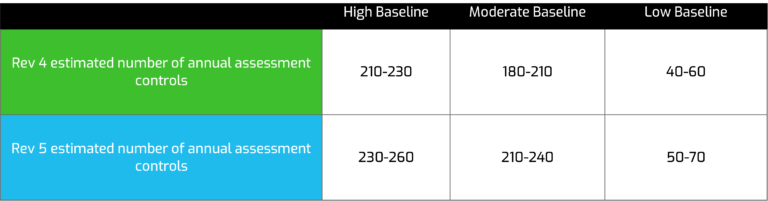
Given the magnitude of Rev 5 changes, material impacts will be segmented into domains in our future blog posts. It will take a combination of all key stakeholders weighing in (especially the CSP community) to ensure all are clearly understood and impacted.
Key Point 3: Impacts to Documentation and Authorization Boundaries
The points below are the actions a CSP will need to undertake so that the CSP is well prepared for the Rev 5 assessment.
- Update technology – many controls such as AC-4(4) and SI-4(10) require a CSP to implement either a new technology or implement new features to an existing technology. At a high level, this requires packets to be decrypted, evaluated, and re-encrypted before final destination delivery.
- New Controls and Parameters – each baseline introduces new controls and parameters; for example CM-6, CA-8(2), and the SR/Supply Chain Risk Management family. The CM-6 control requires the CSP to now use the DISA STIGs instead of the CIS Benchmarks, the CA-8(2) control requires the CSP to perform red teaming activities, and the SR family is a net new control family requiring the management of Supply Chain risks. All of these controls, plus a few others will be explored in upcoming Fortreum informational releases.
- Update the System Security Plan (SSP) –there are a significant number of new controls, as well as controls that have undergone parameter changes. Before any assessment begins, the CSP will need to do the following: Download the new SSP template from the FedRAMP website once posted (templates are not posted yet)
-Update current implementations within the Rev 5 SSP to match FedRAMP-required parameters and requirements
-Address/document all new controls
- Update Policies and Procedures – updating all ancillary documentation outside of the SSP to address all FedRAMP required NIST 800-53 Rev 5 parameters. This includes, but is not limited to, the security policies and procedures (-1 security controls), the Contingency Plan, the Incident Response Plan, the Configuration Management Plan, training material, and the penetration testing requirements to meet CA-8(2).
It is critical that all of these activities are completed before undergoing a FedRAMP assessment. If an assessment begins and these activities have not been properly performed, the assessment may result in numerous failures that would be marked as POA&Ms. As an example, if technology is not updated (see bullet 1 above) and does not meet FedRAMP-required parameters during testing, then the CSP authorization or continued authorization may be at risk.
Key Point 4: Impacts to Penetration Testing and Vulnerability Scanning
The move to Rev 5 does not appear to impact existing penetration testing or vulnerability scanning activities. (one exception) This includes existing web applications, databases, operating systems, and container scanning processes. CSPs should continue their current, FedRAMP-compliant penetration testing and scanning activities, as is while ensuring they are following the latest guidance from the FedRAMP PMO, as the FedRAMP Penetration Test Guidance was updated in June 2022.
One key new addition under Rev 5 is the CA-8(2) security control. CA-8(2) requires Red Teaming exercises. However, it is not clear at this point if the Red Team Exercise is required to be performed by a 3PAO, the CSP, or both.
Similar to when FedRAMP transitioned from Rev 3 to Rev 4, the key aspect of the transition is having a sound plan/approach to make the transition. Some organizations have waited until the control set is final and some have undergone mock internal audits anticipating the draft changes (when it was close to final). Follow the key foundations below for making the FedRAMP Rev 5 transition a success:

Be on the lookout for more content regarding the Rev 5 transition. We’ll be highlighting some of the more complex/material impacting FedRAMP controls that are new with the Rev 5 release. Interpretations will need to be normalized and defendable, so get ready for some healthy discussions.
Fortreum is the fastest growing FedRAMP 3PAO in the marketplace and have collectively worked on FedRAMP engagement lifecycles since the inception of the program. Leverage us as a sounding board for your FedRAMP transition strategy. If interested in learning more, you can reach out to Compliance@fortreum.com and we’ll connect you with an expert.











