Initial Background
In the early life of FedRAMP, situations were arising where Third-Party Assessment Organizations (3PAOs) were assessing Cloud Service Providers (CSPs) that were not fully prepared for or did not completely understand the security requirements set forth within NIST Special Publication 800-53: Security and Privacy Controls for Federal Information Systems and Organizations. This resulted in Security Assessment Reports (SARs) with many findings, and oftentimes resulted in a unfavorable recommendation (DENIED) from the 3PAO. So now you have a CSP who may not have understood how to implement the requirements correctly to begin with, being handed a report stating they have more work to do to prove that they are secure enough to handle federal data. FedRAMP had to figure out how to determine if CSPs were technically prepared for a full security control assessment while also providing better awareness earlier in areas where they may need to improve or strengthen their security posture. Thus, the FedRAMP Readiness Assessment Report (RAR) was born.
What is the Readiness Assessment Report (RAR)?
The purpose of the RAR is to give you a taste of what the assessment is like, while not requiring you to be as rigorous as an initial security control assessment would be. Both assessment processes are similar in terms of interviewing personnel, collecting evidence, and writing up results in reports. The RAR does not cover all FedRAMP baselined security controls that an initial assessment would, rather a selection of the most important controls related to security to determine overall readiness. While evidence may be collected by the 3PAO during the RAR engagement, it is not presented with the report like it would be with the SAR in an initial assessment.
“Think of the RAR as a technical validation. It’s a pre-requisite validation on key FedRAMP technical areas to let CSP’s know if they’ve met the bar. As an added bonus, if your cloud service offering is deemed FedRAMP Ready, you get listed in the FedRAMP Marketplace”
The RAR is designed for an organization that is ideally 80% (or more) ready for an initial assessment. Their environment would be built and hardened from a technical perspective, fully complying with the NIST security control requirements. The gaps in compliance would theoretically be managerial or technical in nature. For example, the CSP’s documentation may still be in draft form and not considered final. Gaps that would not be considered major fixes and impede their ability to ensure their environment remains secure.
Preparation for a RAR can be just as much work as preparation for an initial assessment. Remember, the information in the RAR is designed to assist in answering questions during the assessment so it can allow organizations to become more prepared and understand what evidence they need to prove what should be in place. The same can be said for any deficiencies – the RAR will reveal any flaws that can be found so that they can be remediated before moving onto the assessment phase. Additionally, evidence collected by the 3PAO during the RAR assessment has the potential to be reused during the initial assessment if it meets the FedRAMP timeliness requirements. (CSP Timeliness and Accuracy of Testing Requirements)
Key Concepts
If you want to provide IT/cloud services to US Public Sector entities, your system/s must meet security standards set at the Federal, State and Local level. Let’s take a quick look at some (not all encompassing) of the regulated standards we see for cloud systems and general requirements.
- The Authorization Boundary: If you ask any 3PAO assessor what was the most crucial element of a RAR, what response would you get? They would all respond with the same answer: a fully accurate, complete, and understandable authorization boundary diagram.
Ensure your environment is logically separated from non-FedRAMP tenants and data. Co-mingling of non-FedRAMP tenants and data with FedRAMP tenants and data is a huge red flag to FedRAMP. Your diagram should show this in detail and be easy to understand how this is achieved.
Expect to spend a lot of time with this diagram, going through multiple iterations with your own organization, the 3PAO, and FedRAMP until it is considered final as it helps inform many other sections of the RAR.
It is going to be one of the items that FedRAMP scrutinizes the most. There have been many RAR briefings where the PMO members have drawn portions of the boundary out on a white board and asked for clarification or understanding.
Most importantly, ensure it is accurate above all else. If the diagram has outdated tools or software, ensure they are updated to reflect these changes. This is an easy way to prevent unnecessary confusion. - No Hypothetical Systems or Systems Under Development: This is a simple concept. If your system is not considered fully operational then how can you know it is ready to be assessed in its an actual state? Do not begin a RAR until the system is technically ready for the assessment.
- Details: The RAR template can be sneakily deceptive. the Moderate RAR clocks in at 30 pages, which does not seem like it requires a lot of information. A comprehensive report including the diagrams is going to be somewhere near 60 pages or more when complete. The RAR is going to require an organization to be more detailed than the initial assessment because the 3PAO will have to explain how, in their eyes, the CSP is ready to be assessed, what makes them ready, how the 3PAO came to that conclusion, and any issues the 3PAO found with the question being asked of your organization.
- Section 3 is where the largest amount of detail is going to be provided. It is where all the information about the system is provided and expanded upon, including what your organization considers its boundary, how it communicates inside and outside its network, how data flows, how data and users are separated physically and/or logically, and how it uses any other FedRAMP authorized products or services.
- Federal Mandates: The RAR contains six (6) requirements that FedRAMP has deemed as non-negotiable. Meaning that an organization must be fully compliant in all six, there are no alternative implementations or wiggle room with the mandates. They are strictly pass or fail. If an organization is not fully compliant with the federal mandates, they do not move forward in the RAR process.

- FedRAMP Requirements: This section follows right after the Federal Mandates section and just like that one, your organization must be fully compliant in all five (5) of these requirements as well. This section is asking if your organization is using FIPS 140-2 Validated Cryptographic Modules.
- If an organization has answered Yes to Question 1 in the Federal Mandates section, then all the answers should be Yes in this section as well. The distinction has been made here because organizations can start to get confused by seeing two different sections one right after the other where they must answer in the affirmative for every requirement.
- The importance of the System Security Plan (SSP) and documentation in general: The SSP is arguably one of the most important documents a CSP and a 3PAO can both have in their possession. It serves as the guidebook explaining what process your organization has in place to comply with the required security control. The RAR does a poor job at underscoring the importance of this document, only asking the 3PAO to highlight how complete the SSP is and identify where controls are categorized outside of the expected norm of “Implemented”.
“This clearly was noticed by FedRAMP as last year they released the 3PAO Readiness Assessment Report Guide which clarifies that “if a CSP has not begun documenting an SSP – or even have a majority completed – then they would not be “ready” for a FedRAMP assessment.”
- Additionally, FedRAMP goes on to highlight the importance of mature processes and procedures and having those documented as well. Stating that “if they do not have a majority of their processes and procedures written, a CSP would not have a mature organization.”
- Answering No is not a bad thing: As it has been said before, the intent behind the RAR is to determine assessment readiness. If an organization answers No to a response, it assists in identifying an area where they need to dedicate resources and assign actionable tasks to resolve that gap. The only times that No becomes an issue are when an organization answers No to a control requires a Yes response only, or when the No responses outnumber the Yes responses.
Key Considerations
- Time Considerations
- We cannot tell you how many kickoffs our assessors have been on with clients and their first words are “We want to be FedRAMP authorized by this date.” Obviously, an end goal needs to be kept in mind, but that goal needs to factor in going through multiple iterations, possible delays, updates, remediations/fixes, and more.
- For instance, FedRAMP in the 3PAO Readiness Assessment Report Guide that they estimate typical LOE will between 2-4 weeks for the 3PAO to gather information, write it up, and compile the initial report. It says nothing about what happens after the initial report. It assumes an organization has everything in place and is fully ready to be assessed. It does not factor in any further updates needed to be made because of changes due to major findings, PMO meetings, agency meetings, etc. The timeline could grow from 2-4 more weeks to 2, 3, 4+ more months. The RAR will continue to go through multiple iterations until FedRAMP is happy with the result. And now you see how quickly and easily the timelines can diverge.
- Engagement Lifecycle Process – ultimately, FedRAMP Readiness drive how long this process will take. We’ve outlined the steps below with more focus on the process versus timelines.
- We cannot tell you how many kickoffs our assessors have been on with clients and their first words are “We want to be FedRAMP authorized by this date.” Obviously, an end goal needs to be kept in mind, but that goal needs to factor in going through multiple iterations, possible delays, updates, remediations/fixes, and more.
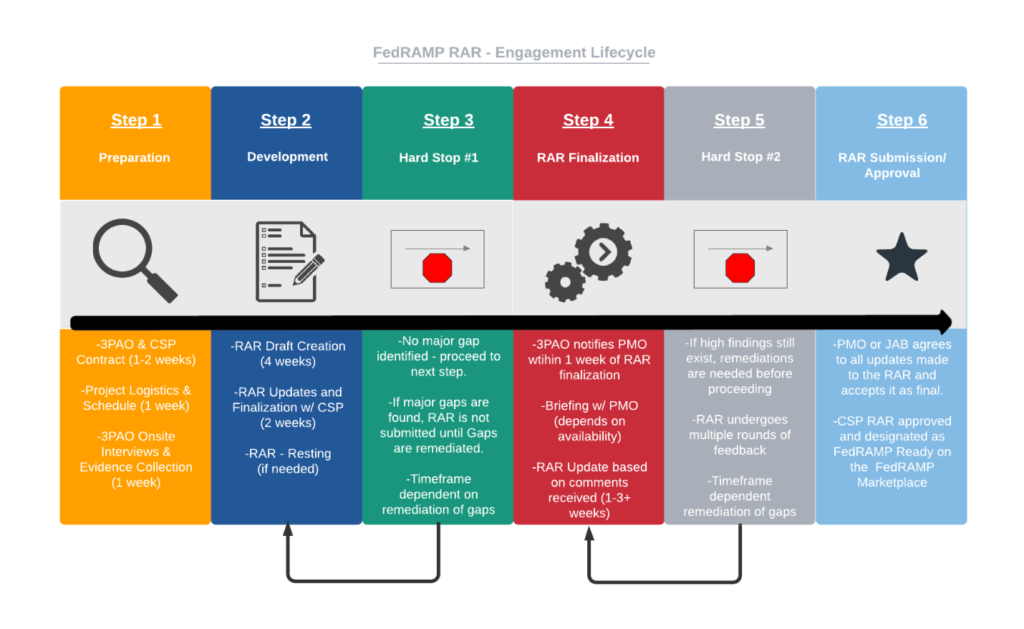
- Transparency is Key
- It is important to be honest where your organization is in terms of how ready you are for a RAR. If you are still in the development stage of their system, or most of your documentation exists in the heads of your personnel rather than on paper, or you do not know much about NIST SP 800-53, then you should not be going through the RAR process because it is going to be a difficult and confusing time for you. The assessor should not be educating your organization every step of the way. Instead, the idea should be that your organization should be fairly educated already, just maybe lacking an expert to give you a more detailed guidance in how to make sure you are ready for the RAR.
- The best way to determine your overall readiness is to try completing the RAR as an internal self-assessment activity. This will allow you to best understand where you stand against the requirements from your own viewpoint. While maybe not fully aligned to that of a 3PAO, it is at least a good starting point to make the decision on when to schedule the 3PAO.
- Penetration Testing
- While not explicitly stated by FedRAMP within the RAR, an organization should have a penetration test conducted prior to beginning the RAR process. In fact, the NIST control requiring Penetration Testing (CA-8) does not appear at all in the document. Penetration testing is mentioned only once in the RAR, and that is within the 3PAO instructions for testing Separation Measures. This is another one of those concepts clarified in the 3PAO Readiness Assessment Report Guide where FedRAMP states the following: “It is a best practice and ultimate requirement of FedRAMP to complete a penetration test. However, for a Readiness Assessment, this is not an explicit requirement. FedRAMP recommends that a Penetration Test be reviewed – even if completed by the CSP or another assessor.”
- Federal Mandates Are a Must
- o As mentioned earlier, all federal mandates must be met. This is an absolute dealbreaker. In fact, your 3PAO cannot even submit the RAR to FedRAMP if you are not meeting all federal mandates. If you cannot meet all of these before engaging your 3PAO, don’t even bother to schedule the assessment. The most common misinterpreted mandate is the one with regards to FIPS 140-2 validated encryption. This must be in place at all entry/exit points of the boundary, as well as internally in transit and at rest.
Summary
Navigating the FedRAMP process is no easy feat no matter the size of your organization. The Readiness Assessment Report process is designed to ease some of the pitfalls that an organization can experience while navigating the process. Overall, it has done a great job at ensuring organizations are ready to be assessed making for smoother initial security assessments, but it is not a perfect process by any means. Much like the RAR itself, the process is iterative and thus constantly changing as the security needs of the government change as well. Hopefully, this article leaves you feeling more knowledgeable about how to approach a RAR and provides your organization with areas to pinpoint its focus. If you have additional questions, feel free to reach out to us and we can put you in contact with one of our senior assessors who have hands on experience performing readiness assessments.











