Commercial cloud service providers (CSP) must achieve a FedRAMP authorization to initially sell and expand their footprint for US government entities. One of the bigger obstacles in achieving a FedRAMP authorization is a successful implementation of FIPS 140-2 validated technologies (security requirements for cryptographic modules) within their cloud service offering. The topic area is complex and commonly misunderstood – lets dig deeper into our understanding and how to apply it.
FIPS & FedRAMP Primer
We often get asked what the most critical areas are in achieving a FedRAMP authorization in terms of authorization showstoppers. There are plenty of architecture elements to consider but one of the most complex and highly scrutinized requirements is around a successful implementation of Federal Information Processing Standards Publications (FIPS) 140-2 technologies. What does it mean to implement FIPS 140-2 validated technologies into a cloud offering and what is the difference between FIPS validated and FIPS compliant? Ensuring that CSPs are adhering to the FIPS 140-2 validated standard (soon to be FIPS 140-3 for the FedRAMP program) is a critical element in FedRAMP authorization success. Matter of fact, it is a non-negotiable issue for the FedRAMP Joint Authorization Board (JAB) authorizations and most Federal agencies as it is a Federal Mandate requirement as stipulated in the Readiness Assessment Report.
“Lack of FIPS 140-2 validated products is a showstopper for all FedRAMP JAB and most Agency authorizations”
We are going to dive into the basics around FIPS 140-2 & FIPS 140-3, why it is important, the difference between FIPS validated and compliant and how to apply and set the foundation for implementing these complex requirements into existing or future cloud service offering architectures. Future releases of this FIPS and FedRAMP series will also look to apply specific use cases to the major hyperscale cloud providers.
What is FIPS & the difference between FIPS 140-2 and FIPS 140-3?
Federal Information Processing Standards (FIPS) Publications are issued by the National Institute of Standards and Technology (NIST) through the Secretary of Commerce. As part of the FIPS effort, the Cryptographic Module Validation Program (CMVP) validates cryptographic modules to a defined set of criteria and cryptographic standards. In the CMVP, vendors of cryptographic modules use independent, accredited testing laboratories to have their modules tested. National Voluntary Laboratory Accreditation Program (NVLAP) accredited laboratories perform cryptographic module compliance/conformance testing. Products validated as conforming to FIPS 140-2 are accepted by the Federal agencies of both countries for the protection of sensitive information (United States) or Designated Information (Canada).
FIPS 140-2 (existing baseline requirement) – leveraging FIPS 140-2 validated products is a hard requirement for the FedRAMP JAB and most Federal Agency authorizations. Very few Federal Agencies approve exceptions, and once approved, they still need to be accepted by the FedRAMP PMO for the system to be listed on the FedRAMP Marketplace as an authorized CSP.
FIPS 140-3 (Upcoming baseline requirement) – FIPS 140-3 replaces FIPS 140-2 and further aligns with ISO/IEC 19790:2012(E) and ISO/IEC 24759:2017(E). Major changes in FIPS 140-3 are limited to the introduction of non-invasive physical requirements.
The FIPS 140-2/140-3 standard provides four increasing, qualitative levels of security: Level 1, Level 2, Level 3, and Level 4. These levels are intended to cover the wide range of potential applications and environments in which cryptographic modules may be employed.
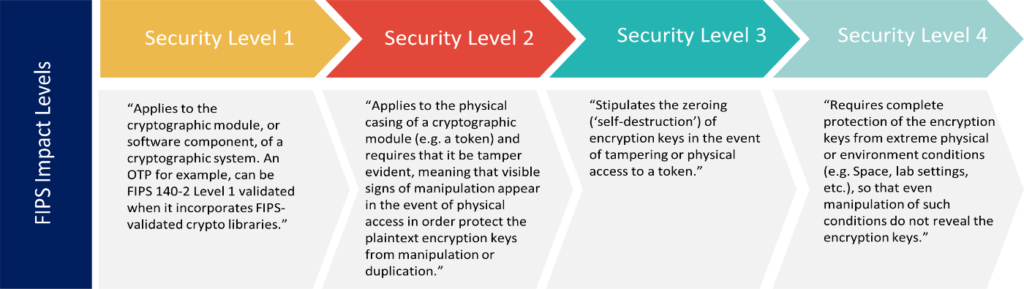
While FIPS 140-2 will be valid for FedRAMP offerings through 2026, the CMVP will only accept applications for FIPS 140-2 validation through September 2021. After that time, all new applications must be submitted under FIPS 140-3 for validation.
FIPS Compliant vs. Validated?
We have had many FIPS discussions with CSPs and the common misunderstandings we come across is on how the FIPS 140-2 requirements are to be applied. Many technology providers will try to claim FIPS 140-2 compliant modules and algorithms are sufficient, versus validated and certified algorithms and modules. The following terms below will help you understand the difference.
- FIPS Compliant: Industry term for technology products in which vendors claim they meet the FIPS 140-2/140-3 requirements (encryption libraries). These products have not yet gone through the full, independent NVLAP review with respective protection profiles. FedRAMP has made it clear that they will not accept products that are compliant only – they must also be validated by an approved NIST NVLAP laboratory.
- FIPS Validated: The software (and/or hardware) must be independently validated by one of 13 NIST NVLAP laboratories. This validation is to ensure the cryptographic module within the product meets all the FIPS 140-2 (and soon to be FIPS 140-3) requirements.
Leveraging a FIPS 140-2 validated product is required, but it does not automatically mean you have met the requirement just because the product is FIPS 140-2 validated. You must also ensure that it is configured to operate in FIPS mode.
FIPS 140-2 Approved Vendors?
Given the complexities of achieving a FIPS 140-2 validation and since FedRAMP requires that all cryptography utilized in the system is FIPS validated and has a FIPS validated certificate number, CSPs can do a quick search in the NIST CMVP for FIPS 140-2 validated modules The National Institute of Standards and Technology (NIST) maintains a current list of all FIPS validated modules and has provided a searchable interface located at https://csrc.nist.gov/Projects/cryptographic-module-validation-program/validated-modules/Search. An advanced search option is also available which can be used to further refine your search criteria
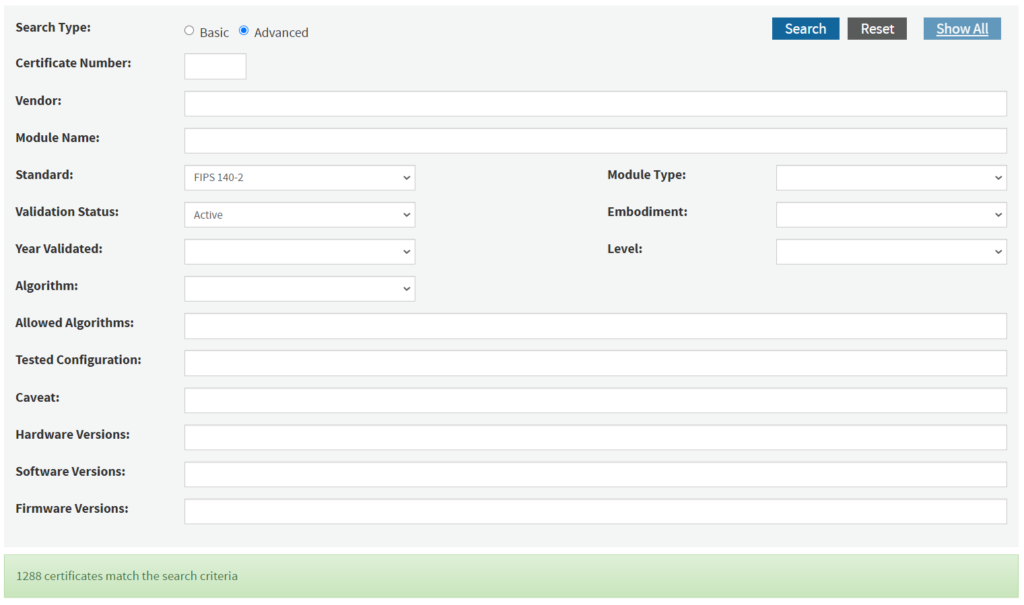
Whether you are a CSP or a FedRAMP advisor/assessor, this is where organizations verify technology products that are FIPS validated. The NIST CMVP site should be utilized as the authoritative source for verifying the FIPS validation of your potential FIPS products and solutions. There is even a search feature for products that are undergoing a validation review and listed as In Process. Potential architecture use cases will be covered in future posts.
Applicable FIPS 140-2 controls FedRAMP?
Let us start piecing together how to better interpret the FedRAMP-related cryptographic security controls with the FIPS 140-2 requirements within an architecture.
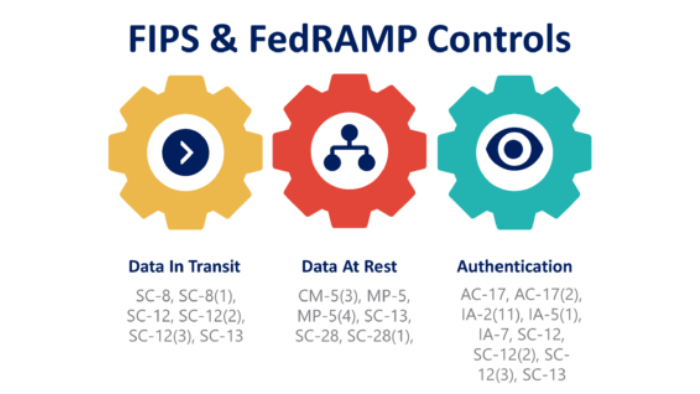
- Data In Transit
- Customer (Web application) – all web application sessions must be encrypted via FIPS 140-2 validated crypto modules.
- CSP administrative (Remote access) – all remote access sessions to the application or underlying infrastructure (AWS, Azure, GCP, IBM, Others) must be encrypted via FIPS 140-2 validated crypto modules.
- Site-to-site replication – all site-to-site replication for disaster recovery must be encrypted via FIPS 140-2 validated crypto modules.
- Data At Rest
- All data at rest must be encrypted via FIPS 140-2 validated crypto modules.
- Authentication
- Authentication must meet the Digital Identity requirements as stipulated in NIST SP 800-63. This publication requires FIPS validated modules for multifactor authenticator (MFA) products.
- Identity Management/Provider must be configured to operate in FIPS mode.
Before we dig too deep in the vendor pool (determining what products to procure) – let us think about where we apply the requirements within a standard architecture. Anywhere that cryptography is deployed, it must leverage FIPS 140-2 validated technologies. There are far more complex architectures out there, but we will start with a simple cloud architecture. Below we have highlighted potential areas where FIPS 140-2 validated controls would apply (at a minimum).
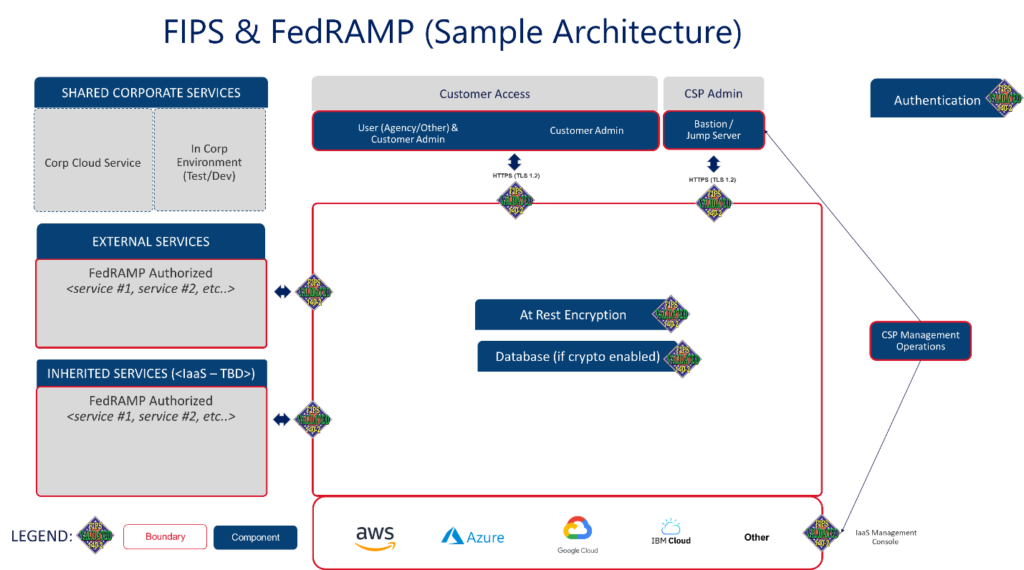
Summary
While the topic of FIPS and FedRAMP has put many people to sleep, it is an absolute critical step in your journey to FedRAMP authorization. Unfortunately, there have been many FedRAMP pursuits that have been abruptly halted due to non-compliance in this area. Make sure that you understand what type of cryptography you have employed within your FedRAMP architecture, where it is applied (at rest, in transit, authentication) and that you are using FIPS 140-2 validated technologies in the proper FIPS mode to meet the requirements.
This document is the first in a series of blog posts specifically targeting the complexities of FIPS and FedRAMP. Next, we will start showcasing different Infrastructure as a Services (IaaS) providers and look to provide practical customer use cases for easier understanding and industry adoption.











