As experts who have conducted hundreds of Red Team engagements across diverse cloud and enterprise environments, we’ve observed that organizations frequently misunderstand the fundamental nature and purpose of these exercises. These misunderstandings can diminish the value of Red Team activities and potentially lead to misaligned security investments.
While Red Team exercises provide unique value in a security program, it’s equally important to understand what they are not. This clarity helps organizations set appropriate expectations and integrate Red Team activities effectively into their broader security strategy. By addressing these common misconceptions, we hope to help organizations leverage Red Team exercises more effectively as part of their security strategy.
Red Teaming is Not a Replacement for Core Security Practices
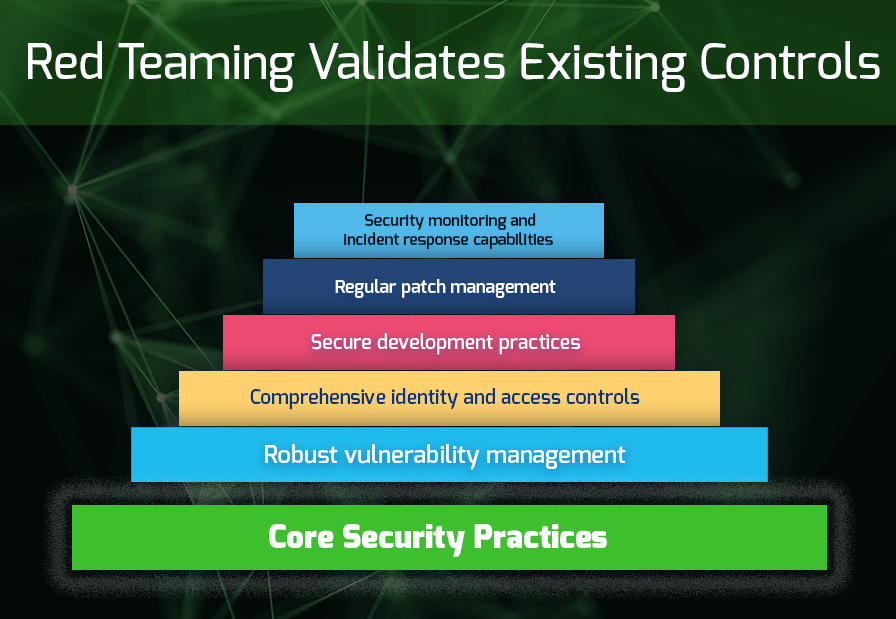 Red Teaming isn’t here to replace your security basics—it’s here to build on them. They validate the effectiveness of your existing controls, but cannot substitute for:
Red Teaming isn’t here to replace your security basics—it’s here to build on them. They validate the effectiveness of your existing controls, but cannot substitute for:
- Robust vulnerability management
- Comprehensive identity and access controls
- Secure development practices
- Regular patch management
- Security monitoring and incident response capabilities
“Red Teaming isn’t here to replace your security basics—it’s here to build on them.”Organizations should view Red Teaming as the capstone of a mature security program—not a shortcut to security maturity. The most successful exercises occur in environments where fundamental security practices are already established, allowing the Red Team to focus on sophisticated attack chains rather than basic vulnerabilities.
Red Teaming Does Not Hinder Operations
Professional Red Teams operate under a “do no harm” principle that prioritizes operational stability. Modern Red Team methodology:
- Avoids disruptive testing that could impact availability
- Coordinates activities with key stakeholders to minimize business risk
- Implements safeguards to prevent accidental disruption
- Maintains continuous communication channels with security teams
The goal is to identify security weaknesses without creating operational incidents. A skilled Red Team must exercise serious discernment when it simulates attacker techniques. They must know what methods minimize the risk of collateral damage while still providing realistic adversarial testing.
Red Teaming Does Not Make Your Environment More Vulnerable
Red Teams reveal existing security weaknesses—they don’t create new ones. Professional Red Teams:
- Remove all testing artifacts after exercises conclude
- Don’t leave backdoors or persistent access (unless specifically asked to do so)
- Document all actions taken during the engagement
- Secure findings and evidence with the same care as production data
- Provide detailed remediation recommendations for all identified issues
Every finding represents a vulnerability that was already present and potentially exploitable by sophisticated attackers. By discovering these issues under controlled circumstances, you gain the advantage of addressing them proactively rather than reactively after a breach.
Red Teaming is Not an Ad Hoc Activity

- A side project for your existing security team
- A role that can be assigned to any security professional
- An activity that can be performed without specialized training and tools
- Simply running automated tools against targets
“Red Teaming requires specialized expertise that can’t be substituted or improvised.”The expertise required for effective Red Teaming represents years of focused experience in offensive security, combined with specific knowledge of cloud service provider environments. This specialized capability ensures exercises deliver meaningful results that accurately reflect your security posture against sophisticated threats.
Red Teaming is Not a One-Time Event
A single Red Team exercise provides a snapshot of your security posture, but the threat landscape continuously evolves. Effective Red Team programs establish:
- Regular exercise cadences based on your risk profile
- Mechanisms to validate program
- Continuous feedback loops with defensive teams
- Progressive scenario complexity that evolves with your security maturity
Organizations gain the most value when Red Teaming becomes an integrated component of their ongoing security validation strategy rather than an isolated event. Integrating regular exercises—through an internal team or a trusted services provider— as part of ongoing security validation creates a continuous improvement cycle where security posture strengthens incrementally with each exercise, building institutional knowledge and defensive muscle memory. Regular red team engagements provide tangible metrics to demonstrate security ROI to leadership, validate previous remediation efforts, and help mature incident response capabilities through repeated practice. The cumulative insights gained through recurring exercises offer far greater strategic value than what can be achieved through an isolated exercise.
Incorporating Red Team Exercises into Security Strategy
When properly understood, Red Team exercises bridge theoretical security controls and real-world resilience. By recognizing what these exercises are not, organizations can position them strategically within their security framework – not as standalone activities or replacements for fundamental controls, but as integral components of a continuous validation cycle.
“Red Team exercises bridge theoretical security controls and real-world resilience.”
For cloud service providers and enterprise operations, this approach transforms security from a compliance exercise into a competitive advantage. Through properly implemented Red Team programs, you gain what matters most: confidence based on reality rather than assumption.
To learn how to effectively incorporate Red Team exercises into your security program, including optimal timing, target selection, and operationalizing findings, read our upcoming companion post “Red Teaming Reality: Shattering Security Illusions Before a Breach.” There, we will provide a strategic framework for maximizing the value of Red Teaming as part of a mature security strategy.
Fortreum is an independent firm specializing in audit, advisory, and technical testing services, delivering cybersecurity expertise in highly regulated industries. Our mission is to simplify cloud and cybersecurity challenges for our clients. With nearly 25 years of combined experience in both the public and private sectors, Fortreum is dedicated to addressing our customers’ complex cloud and cybersecurity needs.
For more information, visit the Fortreum website or follow the company on LinkedIn at LinkedIn.com/company/fortreum.
Should you have questions about your FedRAMP, XRAMP, cloud and cybersecurity readiness, please reach out to us at Info@fortreum.com or Contact Us at https://fortreum.com/contact/