Introduction
Cloud service providers operate in a complex security landscape where perception and reality can quickly diverge dramatically. Despite substantial investments in security controls, compliance frameworks, and defensive technologies, organizations can maintain the illusory perception of security that is diametrically opposed to what is true in reality; a reality where it’s possible to circumvent security measures through systemic weaknesses in people, process, or implementation. Traditional security assessments—vulnerability scans, compliance audits, and routine penetration tests—frequently fail to identify the complex, multi-stage attack paths that real adversaries leverage, creating dangerous dissonance between real and perceived security.
Red Team exercises cut through the security illusion to the ground truth needed to drive improvement and maturation in a security program. By simulating the tactics, techniques, and procedures of sophisticated threat actors, Red Teams challenge assumptions about security effectiveness throughout your environment, revealing critical insights necessary for meaningful growth. For cloud service providers whose customers entrust them with sensitive data and critical workloads, these exercises offer something beyond compliance checkboxes and theoretical controls: they reveal how your security program actually performs under stress, in a realistic event against a capable adversary, before anything is truly at risk.
“Red Teaming offers more than just a test; it’s a strategic tool to deliver actionable insights before an attacker strikes.”
For security leadership, Red Teaming offers more than just a test; it’s a strategic tool. It delivers clear, actionable insights, showing exactly where resilience needs to be bolstered before an attacker strikes. Application of Red Teaming comes down to this – knowing the truth before it matters, and having the confidence to execute under pressure because your team has been there before. In what follows, we’ll unpack how this approach can transform cloud security, balancing proactive defense with practical outcomes.
Core Benefits of Red Teaming
While compliance frameworks and security certifications provide baseline assurances, they often fail to address the critical question: “Will our security capabilities hold up in a real compromise event?” Red Team exercises provide a type of clarity that can’t be matched with other types of security evaluations or tests. Where traditional assessments often reinforce a false sense of security, adversarial simulation exposes the reality of your defensive posture when confronted with sophisticated threat actors using modern techniques.
“Red Team exercises provide a type of clarity that can’t be matched with other types of security evaluations.”
When a Red Team compromises a developer’s access, leverages that access to extract secrets from a build automation pipeline, and uses those secrets to compromise your production cloud infrastructure, they aren’t demonstrating theoretical risks but exposing actual gaps in your security implementation that shatter the illusion of “compliant” security practices. By systematically probing the boundaries between environments, Red Teams uncover those complex, multi-stage attack paths that real adversaries leverage. Our engagements consistently reveal critical issues at the intersection of corporate systems and production environments—precisely where theoretical models and compliance frameworks fail to capture real-world risk. These boundary-crossing weaknesses represent the exact systemic risks that create dangerous dissonance between perception and reality.
Red Teaming transforms an enterprises security program from a low maturity minimum control-based implementations into a high maturity strategic advantage. It validates whether your security monitoring and response capabilities perform under stress against capable adversaries, delivering the actionable insights security leadership needs. By exercising security functions before breaches occur, you gain the opportunity to address critical control gaps while they remain theoretical rather than after they’ve been exploited. For Cloud Service Providers whose customers entrust them with sensitive data, this isn’t just another assessment—it’s knowing the truth before it matters and building the confidence to execute when real threats emerge.
When to Conduct Red Team Exercises
Effective Target Selection
Effective Red Team exercises require thoughtful target selection that balances realism, scope, and specificity to deliver meaningful security insights. Rather than attempting to test everything, focus on scenarios that mirror genuine threat activity against your operational environment. The most valuable exercises simulate attackers targeting plausible entry points like compromised credentials, vulnerable endpoints, or exposed service accounts—scenarios that reflect how real adversaries would approach your systems. Artificial limitations and exclusions to what’s “in-scope” for a Red Team exercise only serve to attenuate the effect, and impair the result.
“Frame each Red Team exercise around specific questions about your security posture to ensure findings deliver actionable value.”
The most revealing vulnerabilities typically emerge when exercises cross multiple security domains. Design scenarios that test the boundaries between environments—corporate to development, development to production, or across service boundaries—where security controls often differ due to varying operational needs. Our experience shows these transition points frequently contain unexpected attack paths that traditional security assessments miss. By devising scenarios intended to cross these boundaries, you validate whether your architecture truly enforces the isolation it’s designed to maintain or merely creates an illusion of separation that properly positioned attackers can bypass.
Frame each Red Team exercise around specific questions about your security posture to ensure findings deliver actionable value. Instead of generically “testing security,” target scenarios that validate particular assumptions about your defenses: Can an attacker leverage a foothold in your corporate environment to access production data? Would your monitoring detect lateral movement across security domains? Do your identity controls actually enforce proper segregation of duties? This hypothesis-driven approach ensures your Red Team exercises answer critical questions about your specific security risks rather than simply identifying theoretical vulnerabilities, transforming the exercise from a generic assessment into a strategic tool for security improvement.
Operationalizing Red Team Outputs
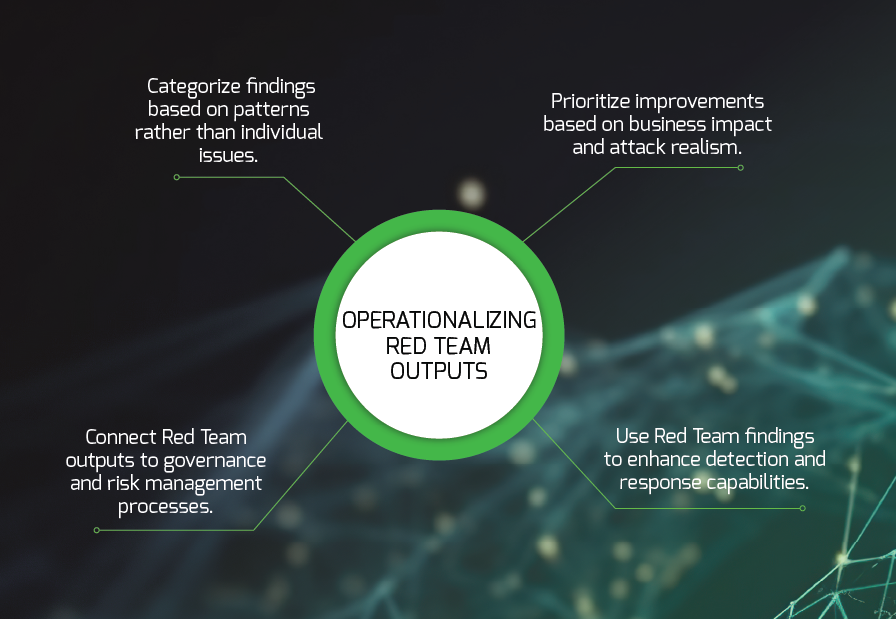
- Categorize findings based on patterns rather than individual issues. Group related findings to identify common themes that reveal broader program gaps—whether in identity governance, boundary controls, or operational processes. Addressing these common sources can resolve numerous technical manifestations simultaneously.
- Prioritize improvements based on business impact and attack realism. Focus first on addressing findings that demonstrate complete attack chains affecting core business functions or customer data. This business-centric approach ensures security resources align with actual organizational risk rather than theoretical vulnerability severity.
- Use Red Team findings to enhance detection and response capabilities. Each undetected Red Team activity represents a blind spot in your security monitoring program. Establish a continuous feedback loop where findings directly inform detection engineering, gradually closing visibility gaps against sophisticated threats.
- Connect Red Team outputs to governance and risk management processes. The strategic insights gained should inform risk registers, security roadmaps, and executive reporting. This integration ensures Red Team exercises contribute to organizational risk management rather than existing as isolated technical assessments.
Conclusion
Red Team exercises represent a powerful strategic tool for Cloud Service Providers seeking to bridge the gap between perceived and actual security. By simulating sophisticated adversaries in realistic scenarios, these exercises reveal critical insights that traditional assessments cannot provide. When properly timed, strategically targeted, and effectively operationalized, Red Team findings drive meaningful security improvements that strengthen your entire defensive ecosystem.
The most successful Red Team programs evolve from isolated exercises into integrated components of a mature security strategy. They create a continuous feedback loop where each engagement reveals new insights, drives targeted improvements, and validates previous remediation efforts. This cyclical approach transforms security from a static compliance exercise into a dynamic capability that evolves alongside threats.
For Cloud Service Providers entrusted with sensitive customer data and critical workloads, this evolution represents more than a security enhancement—it’s a competitive advantage. In an industry where security failures can devastate customer trust, Red Teaming provides something invaluable: confidence based on reality rather than assumption. By knowing your security truth before it matters and dispelling the illusion of false security, you transform your security program from a cost center into a foundation for reliable, trustworthy cloud services that customers can depend on.









