System Development Life-Cycle
Adopting External Supply Chain Service
The Entry of DeepSeek
System Development Life-Cycle
In modern information systems, responsibilities have now fully shifted to embrace the shared service model. Information systems are rapidly shedding the traditional host-based infrastructure model and have completely migrated to service-driven, fully containerized deployments. This shift in the IT ecosystem has brought new challenges, namely System Development Life-Cycle (SDLC) and Continuous Integration, Continuous Delivery (CICD) pipelines being hard pressed to constantly push out new features to keep the service platform dynamic, responsive to client needs, and secured through rapid patches and updates.
Because of this, companies have been looking to third-party software vendors to offload patching, updates, and to facilitate the creation of hardened container packages. An example of this can be seen in the U.S. Airforce’s widespread adoption of Platform One’s Iron Bank service (Platform One | Services | Iron Bank), which is a central repository of pre-hardened container images that agencies regularly pull from to obtain an 80% to 90%” solution.
According to Return on Security (ROS)’s 2024 reporting, the demand for supply chain based security services has risen faster than any other cybersecurity service type in the industry:
Security, Funded #167 – Securing the Bag
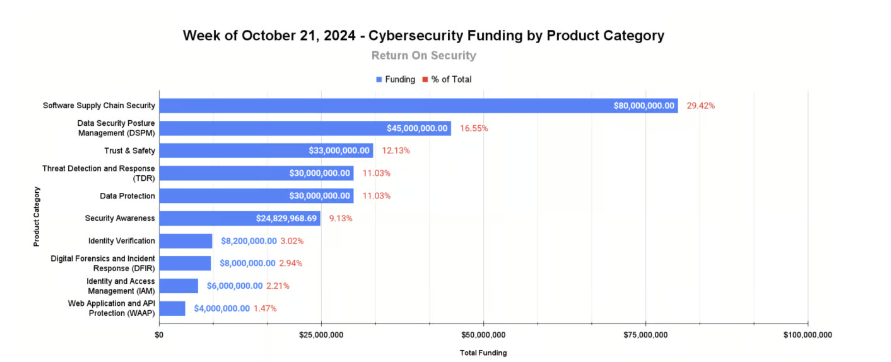
Adopting External Supply Chain Service
As a 3PAO that also performs advisory functions to next-generation systems, Fortreum has seen significant misconceptions that clients have with shared service models when they procure external supply chain vendors. This is especially true for clients that adopt “accelerator” vendors that supply pre-built containers.
When adopting an external supply chain vendor service, it is critical that clients understand the following concepts:
- The client is responsible for the scanning and evaluation of software packages that enter the authorization boundary. The external supply chain vendors do not normally perform this function. This means that the client is still responsible for scanning the provided supply packages as well validating the contents of the supply packages prior to allowing them into the staging environments for testing and deployment.
- Scan requirements include compliance scans ( e.g. STIGs) that are applicable for any applicable technologies contained within the supply package. Validation requirements involve the evaluation of individual package components and subcomponents to confirm that they are not counterfeits and that they have traceability back to a reputable vendor or development team. Validation is usually performed through certificate based code signing, hash-validations, and the use of the NIST Supply Chain Software Build of Materials (SBOM) concepts (Software Security in Supply Chains: Software Bill of Materials (SBOM) | NIST).
- While SBOM has been largely pushed as guidance in 2024 via Executive Order 14028, with the advent of additional NIST SR control family checks, it is quickly accelerating to become a soft requirement. Fortreum forecasts that it will soon (potentially within the next year) become a hard requirement that will be driven by changes being proposed through the new NIST Secure Software Development Framework (Secure Software Development Framework | CSRC)
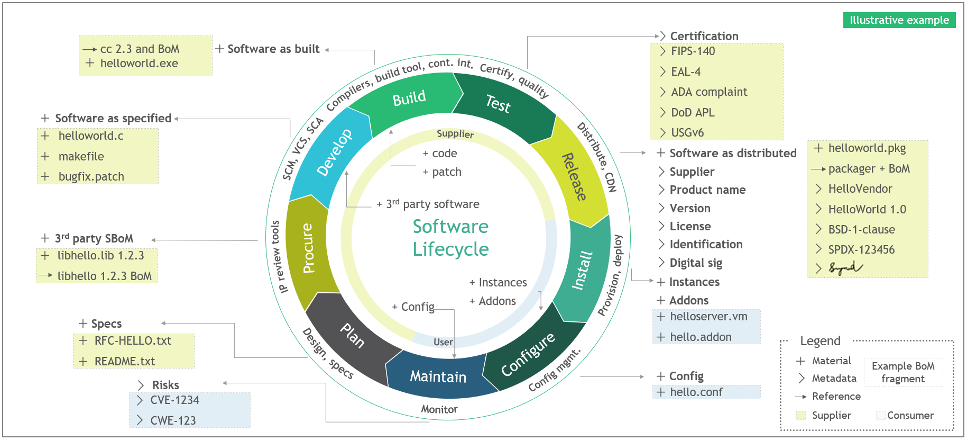
Entering 2025, the risk of supply chain-based threats has increased exponentially through the expansion of the shared service model as well as the introduction of more global players into the supplier market. An example of this can be seen in federal systems and the government directive to evaluate and adopt Artificial Intelligence technology to remain on the forefront of capability. AI and Machine Learning (ML) based capability be entered federal systems through the supply chain. This will occur through software packages that contain AI capabilities pulled from other external models or services (e.g. OpenAI, AWS Bedrock, Oracle Generative AI, Nvidia AI capabilities such as Morpheus, and open-source capabilities such as Ollama). Because of this, the supply chain is the front line defense against modern threats associated with rapid technology adoption.
The Entry of DeepSeek
In addition to the above, new players are entering the AI and ML capabilities market. As of Jan 27th, the market was roiled by the entry of DeepSeek, which is a China-based AI capability that is in direct competition with other global AI producers that are U.S. based or that have U.S. based regulations applied. With the risk of unregulated cutting-edge technologies entering the market, it is critical for organizations to evaluate their supply chains for security hardening, NIST compliance, and alignment with EO 14028 SBOM principles. Stringent government audits and evaluations are on the horizon with the NIST rework of the SSDF (driven by Executive Order on Strengthening and Promoting Innovation in the Nation’s Cybersecurity | The White House) and the mandate for CISA to take a direct role in evaluating supply chain security through the Repository for Software Attestations & Artifacts (RSAA) Repository for Software Attestations and Artifacts (RSAA) User Guide | CISA.
Is your supply chain and SDLC pipeline ready for the front line? If you are unsure about the security of your supply chain, the associated vendors, or your alignment with SBOM, Fortreum is here to help. Contact our advisory experts today and learn how to future proof your pipeline for the future through our industry experts.
+++++
Fortreum is an independent firm specializing in audit, advisory, and technical testing services, delivering cybersecurity expertise in highly regulated industries. Our mission is to simplify cloud and cybersecurity challenges for our clients. With nearly 25 years of combined experience in both the public and private sectors, Fortreum is dedicated to addressing our customers’ complex cloud and cybersecurity needs.
For more information, visit the Fortreum website or follow the company on LinkedIn at LinkedIn.com/company/fortreum.
Should you have questions about your FedRAMP, XRAMP, cloud and cybersecurity readiness, please reach out to us at Info@fortreum.com or Contact Us at https://fortreum.com/contact/









