Strategy & Planning
The ability to measure the effectiveness of a cybersecurity program requires adequate strategy and planning with key stakeholders ensure business alignment. Solicit feedback and input from IT, sales/marketing and executive management to define company objectives and associated risk. Without an understanding of the business objectives and expectations, the cybersecurity program may be ineffective at a foundational level.

Indicators of Proven Experience
Ensure that your cybersecurity firm has experience in building and improving cybersecurity programs. It’s the right blend of people, process and technology – do they understand the lifecycle? Simply put, not all cyber firms have the experience and knowledge your organization needs.

Regulatory Mandates
A cybersecurity program must take all external requirements such as regulatory requirements, customer expectations and industry standards. Failure to include these requirements may lead to potential reputational harm and considerable revenue loss if a potential customer is unable or unwilling to utilize your products or services. Ensure that all industries your organization is selling into have the right regulatory approvals to conduct business.

Program Assurance
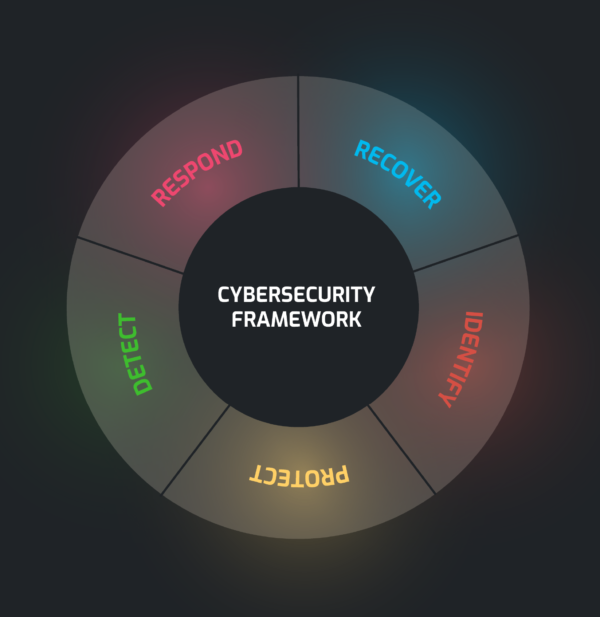
Gaining an understanding of how your organization’s cybersecurity program performs is an effective way to determine overall company risk. Many businesses invest considerable resources & personnel into a cybersecurity program, but fail to ever assess its effectiveness. Hiring an independent organization to assess the cybersecurity program provides unbiased and actionable information needed to validate your program.