In the digital world that we live in, businesses must navigate the complexities of digital transformation while keeping the cost vs. benefit approach to building a comprehensive cybersecurity program. More specifically, economic prosperity of the United States depends on the resiliency of its critical infrastructure and respective protections. When evaluating security program approaches, there are plenty of security frameworks out there to leverage (regulated/non-regulated)– which one makes sense for your organization?
We have seen the Cybersecurity Framework (CSF) successfully implemented across private and public sector. CSF can be used to create and strengthen existing risk management programs as well. It should be implemented as a continuous process based on the changing landscape of the organization and threat source adaptations. Let us jump into the rationale and key tenants for a successful implementation.
CSF Explained
In 2013, President Obama issued an Executive Order (EO) 13636 for improving Critical Infrastructure Cybersecurity. The EO outlined the need for the development of a voluntary Cybersecurity Framework (CSF) that provides a “prioritized, flexible, repeatable, performance based, and cost-effective approach” to managing cybersecurity risk for critical infrastructure services. There have also been several other updates to this, with the latest CSF updates (CSF 1.1) in 2018. The good news – there was private and public industry collaboration for the respective critical infrastructure domains. This framework is extensible and has many private sector use cases. The key elements of the CSF are defined below.
- Comprised of Three Segments: the Framework Core, the Framework Implementation Tiers, and the Framework Profiles
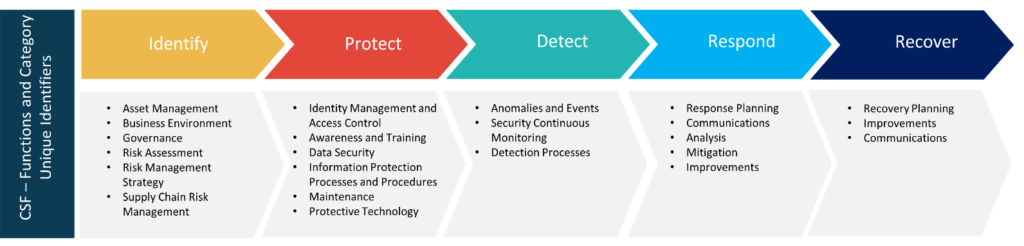
- Key Framework Attributes: Identify, Protect, Detect, Respond, and Recover
- Not a One-size-fits all approach: organizations will need to customize based off the different threats and risk tolerances. It must be adaptive to the organization.
- Voluntary Framework: the CSF was designed for the US critical infrastructure – all cybersecurity recommendations are guidelines to follow versus mandates
“The Framework enables organizations – regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving the security and resilience of critical infrastructure.”
Let us look at the key tenants of the CSF framework outlined below and how it could be leveraged within your organization.
Establishing a Cybersecurity Program
If your organization is examining the CSF as a possible cybersecurity framework to leverage, start with the basic areas to formulate your business case and possible implementation.
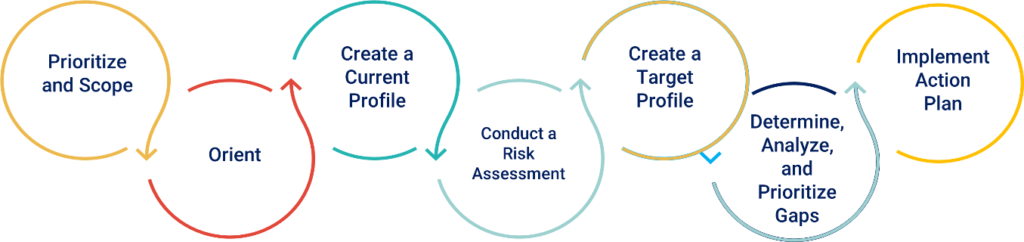
Step 1: Prioritize and Scope
Identify your business/mission objectives, organizational priorities, and scope. Business units may have different business processes and risk tolerances. Make sure you identify key stakeholders within the respective business segments (where applicable) and ensure you have identified interfaces and management buy-in to ensure better commitment and the ability to make change when needed.
Step 2: Orient
Additional review should be conducted to further detail the organizational business segments from a risk perspective, regulatory requirements, systems, and assets. Overall organizational and business segment stakeholders should be consulted to identify current threats and vulnerabilities perspective. Take the time to get know your stakeholders – earn their trust and support.
Step 3: Create a Current Profile
An internal review of the current risk profile should be evaluated (internal audit) to ensure all key stakeholders are clear of the current risk posture and baseline. Leveraging the CSF framework below, give credit where credit is due, even if partial credit, and be honest about what is not currently being done.
Step 4: Conduct a Risk Assessment
There are extensible ways to conduct a risk assessment, tailored as needed, but they generally consist of the following areas within the CSF:
- Know what you have – identify all assets and associated vulnerabilities (scanning, manual validations)
- Threat Intelligence Sources – ensure that internal and external threat sources are identified and applied to your organization
- Ensure that business impacts are clearly outlined in the risk assessment
- Determining risk rating is evaluating “Likelihood X Impact = Risk Rating”
- Define a priority to everything that is identified
Step 5: Create a Target Profile
Now that we know the baseline – lets create a Target Profile using the categories and sub-categories outlined in Step 3. This should be customized based off the organizations risk posture, risk review, governance categories to ensure adequate coverage and risk resilience. Make sure that external connections, supply chain and third-party risk is clearly identified.
Step 6: Determine, Analyze, and Prioritize Gaps
Once the target profile is created – a comparison of the baseline to desired state implementation is conducted. The audit findings against the target profile should be concise, measurable, actionable, time-constrained (based off risks), and have priority assigned to the identified gaps. Associated costs should also be included to ensure there is a holistic picture on what needs to be, and the necessary resources needed to improve overall posture – finding by finding.
Step 7: Implement Action Plan
No more talk – time to act. Now that you have a desired state plan (Target Profile), key stakeholders will need to move forward in remediating identified findings with a continuous improvement mindset. This action plan should be reviewed frequently and updated as the organization and/or threat landscapes change. Continuous assurance is key – point in time evaluations and security posture is not good enough to minimize.
Summary
Leveraging a cybersecurity framework is a good starting point for any organization. It is critical in shaping and optimizing a comprehensive security program for your organization. Customers expect it, your brand requires it, and your reputation is on the line. Organizations evolve over time and the ever-changing risk management should follow suit. Leveraging a security framework like the CSF is good starting point in managing risk for critical infrastructure but also in private sector. It is assumed that control tailoring will be involved to reflect your industry and overall company risk posture but recommended for your business considerations.
Source: Framework for Improving Critical Infrastructure Cybersecurity Version 1.1 National Institute of Standards and Technology April 16, 2018











