Table of Content
What is ConMon?
Receiving FedRAMP authorization is a major accomplishment that can feel like the end of a journey for a cloud service provider (CSP) looking to break into the US Federal marketplace – however, it marks the beginning of a new crucial phase, Continuous Monitoring (ConMon). As described in the FedRAMP Continuous Monitoring Strategy Guide (PDF), ConMon involves the CSP monitoring their security controls, assessing them regularly, and demonstrating that the security posture of their service offering is continuously acceptable. CSPs must conduct activities such as Annual Assessments, Penetration Testing, Vulnerability Scanning, Access Reviews, and more; throughout the ConMon phase. All of the activities mentioned are equally important and provides the CSP’s Authorizing Official (AO) the necessary risk-related information to make risk-based decisions. This blog post will focus on ConMon vulnerability scanning and reporting process, outlining many of the challenges to CSPs are working through.
FedRAMP requires CSPs to execute monthly vulnerability scans and maintain a Plan of Action and Milestones (POAM) to track the identification of vulnerabilities through remediation. Monthly reporting requirements related to vulnerability scanning include submitting scans, POAM, up-to-date system inventory, and documented deviation requests to a CSP’s authorizing agency, the JAB, or the FedRAMP PMO. These activities may seem simple at face value but are consistently challenging for organizations ranging from hyper-scale CSPs to small startups.
ConMon – Key Tenets
While the resultant challenge for a CSP may vary by organization, based on their people/processes/ technologies, the ConMon key tenets must be consistent due to FedRAMP’s high expectations around success criteria and metrics. The graphic below captures the monthly reporting requirements from an overall process perspective.
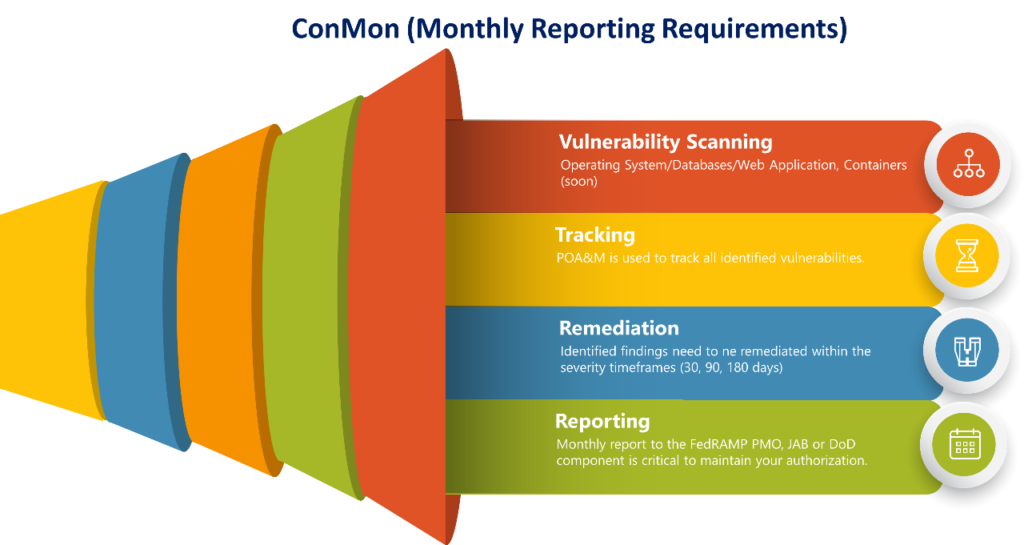
Vulnerability Scanning
Reviewing each step above will provide insight into FedRAMPs criteria and metrics, which has challenged many CSP’s. Scan requirements have been well-defined over the years via FedRAMP and PMO guidance. During the Initial Assessment, a CSP will be tested on the success of their vulnerability scanning program to ensure that 100% of the system inventory is scanned with 100% authentication success. The scanning tools must cover the core asset classes (Operating Systems / Databases / Web Applications (soon Containers!), and the scanner definitions for checks must be up-to-date. In each month after authorization, these scans must be executed and submitted to the FedRAMP PMO. There are a wide variety of complications that CSPs may encounter as they scan their environments, such as:
- Drift often occurs with systems being spun up or down
- Authentication records may expire or lockout
- Network changes may interrupt traffic or block key ports
- Leveraging tool-provided options for review of success and performing manual (or scripted) analysis to ensure breadth & depth of scans is critical.
Tracking
Tracking identified vulnerabilities through remediation can be a challenge for many CSPs, especially hyper-scale providers. The POAM is an essential document used to track all identified vulnerabilities within the system and provides the AO visibility into changes that could negatively impact the system’s overall risk posture. Vulnerability scanning results are tracked within the POAM and have due dates defined from the date of discovery and severity level assigned. High severity vulnerabilities must be remediated within 30 days, Moderate severity vulnerabilities within 90 days, and Low severity vulnerabilities within 180 days. Tracking these vulnerabilities and ensuring none become overdue can be a daunting task.
This brings us to deviation requests – a mechanism for submitting justification and evidence countering the original risk or due-date. There are three types of deviation request: False Positive, Operational Requirement, and Risk Adjustment. False positive is indicates that there is no risk to the system. Risk adjustment means that there is less risk than the scan tool initially identified. Operational requirements mean that the risk will remain, typically with mitigating factors, based on a business or system requirement that outweighs that risk. Many CSPs have developed mature processes for communicating identified vulnerabilities with system administrators and developers for their expert feedback. Properly utilizing these deviation request types with well-written justifications and satisfactory supporting evidence can significantly reduce the perceived risk of your system and help avoid disciplinary action from the FedRAMP PMO for overdue vulnerabilities or a spike in unique vulnerability count.
Remediation
Remediation of identified vulnerabilities requires the owner of the POAM and technical staff responsible for system maintenance to work closely together. CSPs are more likely to meet FedRAMPs remediation requirements if they establish internal vulnerability management policies and procedures that identify stakeholders, sets remediation thresholds, and establish vulnerability management as a priority. CSPs should conduct scanning early in their scan cycle to identify issues such as a single host that has missed a critical patching update. It also allows the CSP’s compliance personnel to develop deviation requests that may address a near-overdue issue.
Reporting
CSP must report their system’s security state to their authorizing agency, the JAB, or the FedRAMP PMO monthly. In regards to vulnerability scanning, CSPs must submit scans, evidence high-risk vulnerabilities are mitigated, POAM, up-to-date system inventory, and documented deviation requests. CSPs should work closely with their authorizing organization to determine the exact method for scan and evidence submission.
Summary
Overall, the key to a successful ConMon program is cultivating a collaborative and communicative team striving towards the same goal; to prioritize the remediation of identified vulnerabilities within prescribed timeframes. Establishing internal vulnerability management policies and procedures is the first step for a ConMon roadmap. Having the leadership’s support and oversight is a significant factor contributing to maintaining a secure and compliant system.
This FedRAMP Continuous Monitoring blog post focuses on key metrics and processes associated with vulnerability scanning post-FedRAMP-ATO. The next blog post looks to dive deeper into the details of common challenges encountered by CSPs as they navigate the ConMon process – along with examples of how those challenges have been overcome.











