Achieving compliance with the Cybersecurity Maturity Model Certification (CMMC) is a critical milestone for organizations seeking to do business with the U.S. Department of Defense. However, the certification path is often fraught with challenges that can derail even the most well-intentioned efforts. From misjudging the scope of the assessment to underestimating the complexity of documentation and technical controls, many Organizations Seeking Certification (OSC) encounter common pitfalls that hinder progress and increase risk. This white paper highlights key areas where OSCs frequently stumble, such as scoping, the System Security Plan (SSP), bring your own device (BYOD) policies, baseline configurations, and risk management. Within this white paper, we offer insights into how to avoid these missteps. By understanding and addressing these vulnerabilities early, organizations can build a more resilient cybersecurity posture and confidently move toward successful CMMC certification.
Below are five common pitfalls that OSCs should be aware of when pursuing a CMMC certification
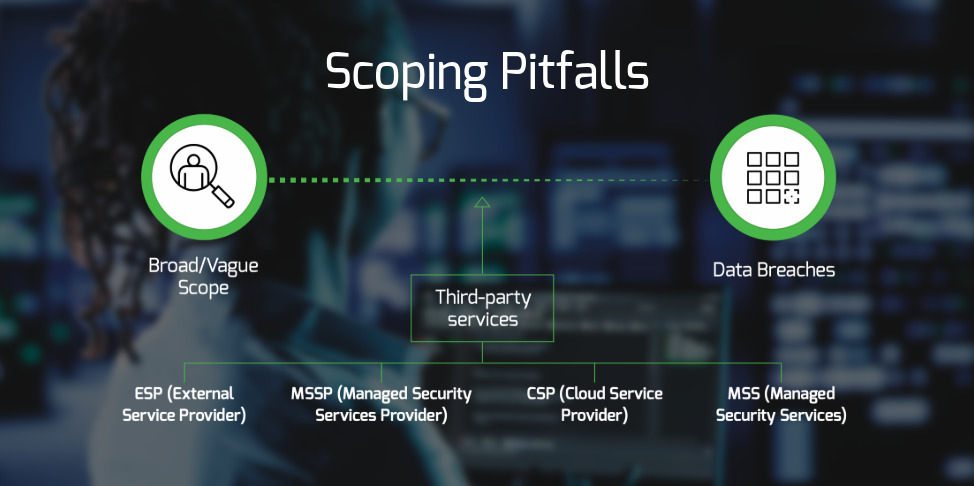
In CMMC assessments, having a well-defined scope is crucial for OSCs. When the scope is unclear, it can lead to compliance gaps, where Controlled Unclassified Information (CUI) may be overlooked. This could result in issues during certification.
A broad or vague scope also increases the risk of data breaches. Without a well-defined scope, it can be difficult to protect CUI information and enforce consistent security controls, which expands the potential for attacks. Additionally, it may be easy to overlook third-party services or cloud environments, leaving vulnerabilities unaddressed. If using third-party services, such as an external service providers (ESPs), cloud service providers (CSPs), managed security services (MSS), or managed security services providers (MSSPs), the OSC must know if any of the third-party service providers process, store, or transmit CUI.
Establishing a clear scope is essential not only for the intent of CMMC and passing the CMMC certification, but also for developing a strong and resilient cybersecurity program that can endure threats and attacks.
SSP Pitfalls
A well-developed SSP is essential for any organization looking to achieve certification. This important document outlines how security controls are put in place to protect CUI. If the SSP is unclear or uses generic language, that will suggest that the OSC may not fully grasp or implement the necessary CMMC practices.
Think of the SSP as a living blueprint of your organization’s CMMC posture. By keeping the SSP accurate and up to date, an OSC can avoid potential issues, such as failed assessments and damage to the OSC’s reputation. A strong SSP is detailed, accurate, and aligned with both operational needs and CMMC requirements. Ensuring that the SSP includes system boundaries, roles and responsibilities, asset inventory, control implementation, and control status, among all other items found in an SSP document, is critical to the success of the OSC pursuing CMMC accreditation.

Bring Your Own Device (BYOD) Pitfalls
While BYOD, such as cell phones and computers, certainly has its positive attributes from a company perspective (cost savings, user familiarity, increased productivity on the go, etc.), there are challenges that arise when trying to implement CMMC level 2 controls. For one, security control implementation on personal devices causes varying challenges for both the company and the device owner. BYODs that are considered in scope would require many CMMC Level 2 controls to be implemented. Examples of these may include encryption standards, configuration controls, and monitoring. The ability to control the device via mobile device management (MDM) also causes potential privacy issues. The device owner may resist solutions that access personal data or can wipe the device clean. Another potential issue is that device owners inadvertently introduce vulnerabilities through the use of unapproved apps or software, weak passwords, or failure to update software. Though the use of BYOD is not a CMMC automatic failure, it can prove to be challenging to implement and secure if not managed correctly.
Configuration Management (Baseline) Pitfalls
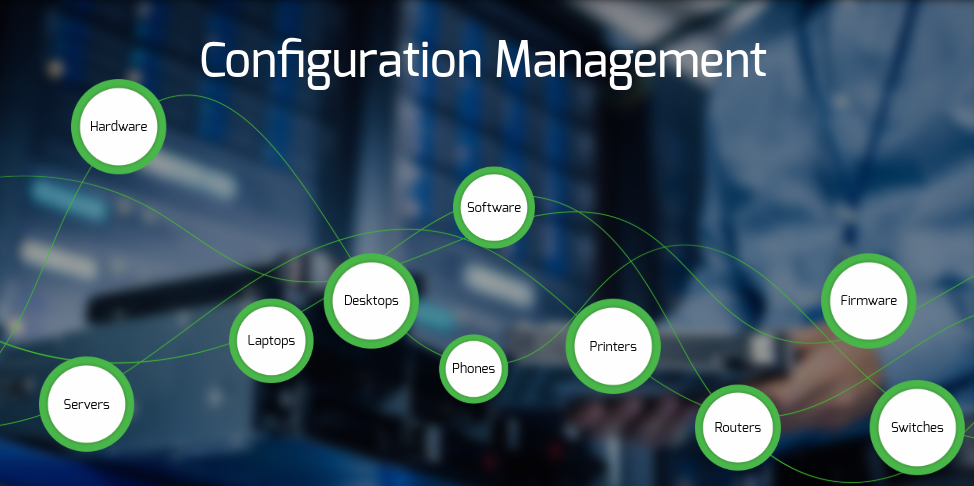
The baseline configuration requirement seems simple enough to understand what products and services you use and deploy them to new IT equipment with a minimum security baseline. While this practice may be acceptable in specific environments, in the context of CMMC Level 2, it could not be further from the truth. All too often, OSCs do not fully understand the complexity of the baseline requirements. It requires not only an asset inventory list, but also the minimum requirements (hardware, software, firmware) needed for a device to be placed in service within the network. This applies to all IT devices an OSC may utilize (servers, laptops, desktops, phones, printers, routers, switches, etc.). It is also important that minimum baseline requirements are maintained and updated as necessary to keep up with the fast pace of evolving technology. It does not take long for a baseline configuration to become obsolete or outdated. Keeping a close eye on baseline configuration standards can help sidestep any potential negative impacts on an organization from technology degradation, while allowing this CMMC Level 2 requirement to be implemented.
Risk Management Pitfalls
Effective risk management is essential to an OSC’s ability to protect CUI. Risk management is a strategic process that continuously identifies, assesses, and mitigates cybersecurity threats. Without a structured program, OSCs lack a clear understanding of vulnerabilities and the consequences of a cyber incident.
Inadequate risk management ultimately serves as a warning sign during a CMMC assessment, indicating that the OSC lacks the foresight and discipline necessary to maintain a robust cybersecurity posture. A mature risk management process is essential not just for certification, but also for building trust with government partners and safeguarding sensitive information in an increasingly complex threat environment.
Fortreum's Pitfall Committment
In the journey to achieve CMMC certification, OSCs often face pitfalls that can derail certification efforts. A foundational misstep is failing to properly scope and define systems, users, and data, which can lead to increased complexity and potential audit failures. This ties closely to developing a SSP, which, if not tailored to the organization’s environment, undermines its cybersecurity credibility.
While BYOD offers benefits such as cost savings and user convenience, it presents significant challenges in meeting CMMC Level 2 requirements. Implementing security controls on personal devices can raise privacy concerns and resistance from users, particularly when using tools like MDM systems. Risks include the use of unapproved applications, weak passwords, and outdated software, which can introduce vulnerabilities. Although BYOD is not prohibited under CMMC, it requires careful management to ensure compliance and security.
Baseline configuration may seem straightforward, but it is a complex and intensive documentation requirement under CMMC Level 2. Organizations often underestimate their scope, which includes maintaining a detailed asset inventory and specifying minimum hardware, software, and firmware requirements for all IT devices. These configurations must be regularly updated to stay current with technological advancements, ensuring compliance and minimizing risks associated with outdated systems.
CMMC compliance is about establishing a resilient and sustainable cybersecurity program that protects sensitive government data. Avoiding these pitfalls requires a strategic, organization-wide commitment to security, supported by planning, strong leadership, and continuous improvement. By addressing these areas, OSCs can achieve certification and significantly strengthen the organization’s overall security posture.
Fortreum is an independent firm specializing in audit, advisory, and technical testing services, delivering cybersecurity expertise in highly regulated industries. Our mission is to simplify cloud and cybersecurity challenges for our clients. With nearly 25 years of combined experience in both the public and private sectors, Fortreum is dedicated to addressing our customers’ complex cloud and cybersecurity needs.
For more information, visit the Fortreum website or follow the company on LinkedIn at LinkedIn.com/company/fortreum.
Should you have questions about your FedRAMP, XRAMP, cloud and cybersecurity readiness, please reach out to us at Info@fortreum.com or Contact Us at https://fortreum.com/contact/











