What is the StateRAMP program?
StateRAMP is organized as a non-profit (501c(6)) with the mission to promote cybersecurity best practices through education, advocacy, and policy development. They support their members and work to improve the cyber posture of state and local governments and the citizens they serve. StateRAMP prioritizes helping providers by supplying them with security templates and resources, reducing time to market, and eliminating barriers to access security verification.
StateRAMP was modeled after FedRAMP (Federal Risk and Management Program) and represents the shared interests of State/Local SLED (state, local, education, tribal/territorial) government, third party assessment organizations, and service providers with Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) solutions.
Why Obtain a StateRAMP Authorization?
StateRAMP is a leveraged or shared resource between providers and government entities. By obtaining a StateRAMP authorization, the system will be placed on the Authorized Product List (APL) and anyone seeking your product or service can more easily find what they are seeking. The enhanced visibility and ‘associated trust’ can help grow your customer base more quickly.
SLED clients must ensure security and privacy controls have been implemented and thereby restrict options to verified and authorized products. By utilizing the ‘leveraged’ assessment model, systems built upon other accredited or authorized systems (i.e., IaaS, PaaS, SaaS) can be “assessed once and utilized many”, thereby reducing cost and effort to the system.
It is important to note that StateRAMP ATOs are a lot like FedRAMP JAB ATOs in that they provide authorization to serve all departments, bureaus, non-profits, agencies, and organizations (within the government of the state granting the ATO).
By obtaining a StateRAMP authorization, the CSP demonstrates to potential clientele that specific security benchmarks have been met, providing greater assurance that the data will be protected. Public trust is of paramount concern in today’s marketplace and a StateRAMP authorization helps quickly gain credibility that may not be achievable otherwise.
Fast Track Option
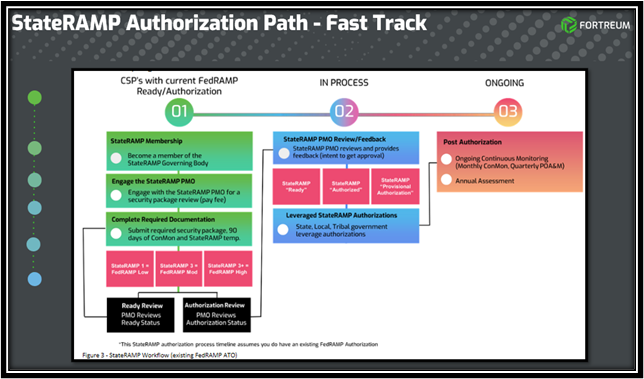
- Become a member
- Engage the StateRAMP Program Management Office (PMO): After joining as a StateRAMP member, service providers must complete a Security Review Request Form to engage the PMO. Prior to their first call with the PMO, they can use this form to provide more information about their company and product.
- Complete required documentation: Service providers should begin working with their third-party assessment organization (3PAO) early in the process to gather and submit the required security documentation, including the provider’s federal-approved security package, 90 days of continuous monitoring, and any necessary StateRAMP templates. The security team at the PMO accepts documents in FedRAMP formatting.
- PMO review: The PMO will review the service provider’s complete security package and conduct a call with the provider and 3PAO to make any final adjustments to the submitted documentation.
- ConMon: Continuous monitoring is required to maintain a product’s security status and listing on StateRAMP’s Authorized Product List. Providers with a federal authorization may submit their product’s monthly reporting to the StateRAMP PMO unless otherwise specified. After the initial assessment is complete, providers must submit their annual 3PAO documentation using StateRAMP templates.
What does the normal authorization process entail?
The process to obtain a StateRAMP authorization is formal and can take a year or longer to accomplish, depending on the maturity of the system. It is important to understand the commitment before beginning as certain delays can derail the process and require starting over, in some cases. There are three (3) core steps consisting of ten key milestones to track the process, as follows (https://stateramp.org/providers/ready-or-authorized-process/):
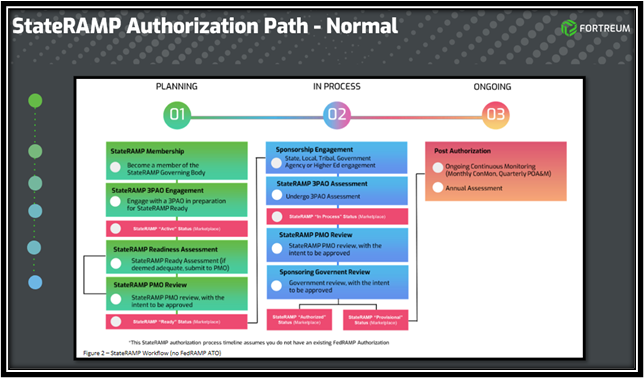
Planning: Become a member
Any SLED government official or employee with responsibility for information security, information technology, privacy, and/or procurement may become a member of StateRAMP. There is no membership fee for SLED entities and individuals can join by registering online.
Service providers interested in becoming a StateRAMP Member should complete the service provider membership form. Service provider membership is available for organizations offering and/or using IaaS, PaaS, and/or SaaS solutions that process, store, and/or transmit government data.
Planning: Security Snapshot
The StateRAMP Security Snapshot is designed to quickly assess the CSP’s (Cloud Service Provider) state and readiness to continue the process. The tool checks key security controls and is similar to a truncated gap analysis assessment wherein the results can advise where to spend time and effort in relation to meeting the Minimum Mandatory Requirements for StateRAMP Ready. The tools available to assist in the assessment process are found at https://stateramp.org/rev-5-templates-and-resources/.
Planning: Understand requirements and resources available
The PMO security team can help guide products through the StateRAMP verification process. The StateRAMP staff currently offers an open forum to discuss questions and concerns on the first Wednesday of each month called “Office Hours”. There is also a video library to help systems begin, including the recorded “Getting Started with StateRAMP” webinar. Finally, most 3PAOs (Third Party Assessment Organizations) that you partner with can help advise and direct you through the process.
Planning: Identify impact level and desired status
The data classification tool is found in the StateRAMP resources library and is utilized to help formalize data classification and thereby advise the overall determined risk level of the system. The following risk categories are possible:

Each category represents a different set of data characteristics and corresponding security requirements ranging from non-private, generally accessible information to protected, personally identifiable information (PII) or classified data.
Planning: Engage a 3PAO
A 3PAO is your partner in guiding and assessing the system against the defined framework and relevant overlay, if applicable. As a current StateRAMP 3PAO, Fortreum’s core goals are to provide experienced assessors to guide you in the process and ultimately assess the system to determine any potential risk that needs to be addressed. We partner with you in working with the StateRAMP’s PMO in risk remediation efforts and ultimately obtaining the authorization.
A list of StateRAMP-Approved Assessors is available on their website for comparison. Once selected, Fortreum will help complete a Readiness Assessment Report (RAR) and/or a Security Assessment Report (SAR) for StateRAMP evaluation.
*Note: as of June 2024, the private cloud authorization option is in-process, not yet available
Planning: Begin working documentation
If a service provider is pursuing Ready status (see below), they must have at least fifty percent of their documentation completed so their 3PAO can complete a StateRAMP Readiness Assessment Report (SR-RAR).
Once a service provider has engaged with a 3PAO to conduct their StateRAMP Authorization Review, the provider must complete a StateRAMP System Security Plan (SR-SSP), StateRAMP Security Controls Matrix (SR-SCM), the Plan of Actions and Milestones (POA&M) document, and any other documentation required by the 3PAO so the 3PAO can complete a StateRAMP Security Assessment Plan (SR-SAP) and a Security Assessment Report (SR-SAR).
In Process: Submit security review request
Before a service provider can submit their completed documentation to the security team at the StateRAMP PMO, the provider must complete the Security Review Request Form. After submitting the form, the StateRAMP PMO team will reach out to schedule an intake call and begin their security review. The process typically takes 2-4 months from this point to obtain an authorization, depending on the state of the system.
In Process: Government sponsor or approvals committee?
A sponsor is a requirement for CSPs to move forward; however, in the absence of a federal sponsor, the StateRAMP Approvals Committee can serve in their place for CSPs who do not have one. Be advised, however, that if a federal sponsor is utilized then the system will be subject to their agency minimum security standards in considering internal policy and procedure.
In Process: Obtain StateRAMP verified status
Once the 3PAO completes assessment and key remediation activities, which generally includes no high findings and overall only moderate to low risk in remaining areas, then the StateRAMP PMO will begin their package review. Once the PMO has evaluated all identified potential risk(s), a follow-up phase begins wherein the CSP and 3PAO work together to address concerns.
Once the StateRAMP PMO has verified all findings, a government sponsor or StateRAMP Approvals Committee accepted the provider’s security package, and all outstanding issues and/or inquiries have been resolved, the provider’s security status on the StateRAMP APL will be changed to ‘Authorized’.
Ongoing: Conmon
Continuous Monitoring (Conmon) is the persistent state that follows authorization, such that the system must be continuously monitored for potential risk. Monthly reporting submissions are made to the StateRAMP PMO that are evaluated and necessary to maintain their StateRAMP security status, as detailed in the StateRAMP Continuous Monitoring Guide.
Risks are tracked in a Plan of Action and Milestone (POA&M); specific requirements depend on the service provider & sponsor. Additionally, there are annual assessments that must be completed by the 3PAO and submitted by the due date to confirm the current risk posture of the system remains within tolerable limits.
Key indicators that you are ready
System assessments can utilize large percentages of security budgets and it is important to ensure the system is ready before moving forward. If a system is not ready, then exorbitant costs can be incurred during remediation and cause delays to the authorization process. It is usually best to take time on the front end of the process to ensure all criteria has been met before rushing to a “hopeful” authorization date.
If the security snapshot has resulted in minimal ‘red flags’, and most, if not all, of the required documentation has been created, then the system is likely ready for full assessment. A full “Initial” assessment can be lengthy and costly, so there is a preliminary step to complete called a “readiness” assessment.
Readiness vs. Initial Assessment
The readiness assessment reviews all key security controls and results in a Readiness Assessment Report (RAR) that details identified concerns and is akin to a gap assessment. The RAR greatly assists in making risk-based decisions in improving the security posture of the system and addressing any gaps in the program that may prevent an authorization. The RAR is conducted by a 3PAO and reviewed by StateRAMP to approve the CSP to move forward with a full “initial” assessment.
Once the RAR findings have been adequately addressed, an initial assessment should be scheduled. The initial assessment goes through every control in great depth and tests the technical implementation of the system. The initial assessment produces the final Security Assessment Report (SAR) that the PMO requires to make their authorization decisions.
StateRAMP Status Delineators
StateRAMP has certain “markers” to identify where a system is in the authorization process. The main tags include ‘progressing’ systems and those that have obtained their authorization. Depending on these two (2) classifications, the following sub-classifications can further denote where a system is in the process:

Authorized Product List (APL)
Once a system begins the process, it will be listed on the StateRAMP Authorized Product List (APL) which is a list of service providers published on the StateRAMP website who have obtained a StateRAMP security status of Active, In-Process, Pending, Ready, Provisional, or Authorized. The StateRAMP APL gives governments and procurement officials confidence in their service provider’s data security capabilities and provides a central location for sourcing service providers using or offering IaaS, SaaS, and/or PaaS solutions that process, store, and/or transmit government data including, Personally Identifiable Information (PII), Protected Health Information(PHI), and/or Payment Card Industry Information (PCI) who are StateRAMP verified. (https://stateramp.org/product-list/)
Conclusion
The decision to become StateRAMP authorized is not simple but can help a company achieve certain goals that may not be available otherwise. Once the decision has been made, it is important to select a partner 3PAO that is experienced and can help you navigate the process in a way that minimizes cost and effort, but the onus remains on the CSP to successfully complete the process. Obtaining authorization is an important step in servicing potential state and local government clientele and Fortreum has the expertise to assist you in this journey.
If you would like to know more about StateRAMP or discuss how Fortreum can help you achieve your goals, inclusive of many other frameworks, please contact us today.
About Fortreum:
We started with a mission to simplify cloud and cybersecurity challenges for our customers. With an extensive track record spanning nearly a quarter of a century across Public and Private Sectors, we possess a keen dedication to solving our customers complex cloud and cybersecurity challenges. Our industry commitment extends to supporting and fostering the development of future cybersecurity experts within our communities. We encourage you to investigate our services further to learn how to leverage cybersecurity as a business enabler.
Should you have questions about your cloud and cybersecurity readiness, please reach out to us at Info@fortreum.com or Contact Us at https://fortreum.com/contact/











